Why understanding Salesforce security is important
Salesforce a powerhouse in CRM solutions, delivering a wide range of digital experiences to its users. Its widespread adoption across industries – and among critical enterprises and governmental agencies – makes it a huge data repository. The goldmine of sensitive data unfortunately attracts money motivated cybercriminals, who today are getting into corporate networks through any channel they can. In other words, they are now only looking at conventional channels like email. Valuable data, operational criticality and the interest of attackers puts pressure on the defenders to gear up on Salesforce security measures.
Shared responsibility model sets the rules in Salesforce data security
Salesforce’s security framework is based on a shared responsibility model. This model defines the security obligations between Salesforce and its users. While Salesforce provides a highly secure cloud infrastructure with plenty of security controls, users are responsible for configuring these settings and mitigating external risks to protect their data effectively. This collaborative approach ensures that every layer of potential vulnerability can be addressed by the correct roles.
Multiple levels of Salesforce data security measures
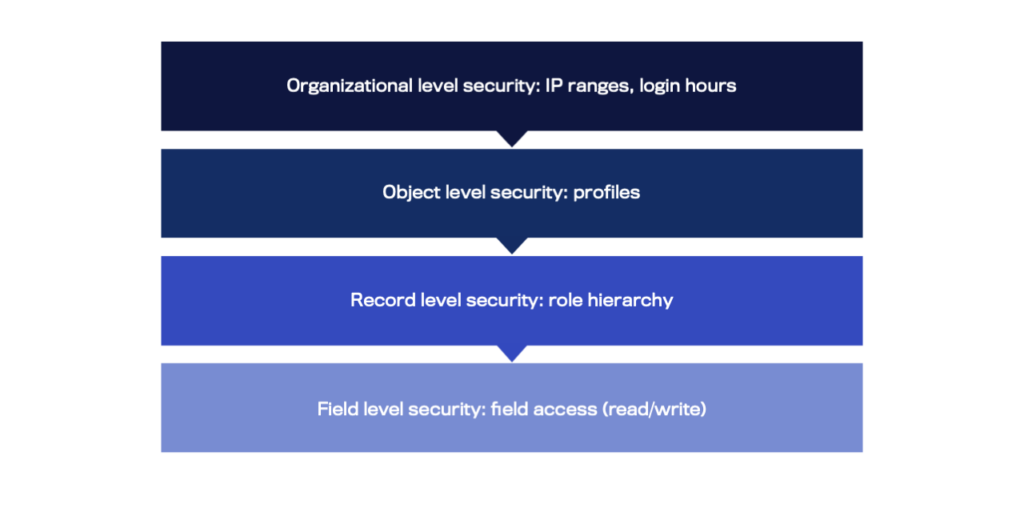
Understanding Salesforce’s comprehensive security setup is crucial for effective data protection. Salesforce structures its security model into four levels to streamline administration and ensure thorough protection:
- Organizational level security: This primary security level involves basic access controls like setting trusted IP ranges and defining login hours to prevent unauthorized access.
- Object level security: At this level, administrators control access to various data sets or “objects” within Salesforce, which can be likened to tables in a database. Modern best practices recommend using Permission Sets for flexible and scalable access management.
- Field level security: This allows admins to control access to specific fields within an object, ensuring users see only the data essential to their role.
- Record level security: This level controls access to individual records within an object. Salesforce offers several methods to fine-tune record visibility and sharing settings, enhancing collaboration without compromising security.
Organizational level security
At the foundational level, organizational security involves securing access to your Salesforce system. This includes setting up restrictions such as trusted IP ranges from which users can log in—accessible via the Login IP Ranges section of a user’s profile. Additionally, Login Hours can be specified to limit user access to predefined times.
To bolster organizational security, Salesforce administrators should enforce strong password policies and consider integrating advanced security solutions like Salesforce Shield and WithSecure’s Cloud Protection for Salesforce.
Object level security
In Salesforce, an object is akin to a database table and houses data sets relevant to specific business functions. Historically, object access was controlled directly through user profiles. However, Salesforce now advises utilizing Permission Sets and Permission Set Groups for this purpose. This approach allows streamlined access management aligned with users’ roles.
Field level security
Field level security pertains to the access controls at the individual field within an object, similar to columns in a spreadsheet. This setup ensures that access to sensitive fields can be tightly controlled and varied between different users, depending on their job requirements. Administrators can configure these settings directly in user profiles or more dynamically through Permission Sets.
Record level security
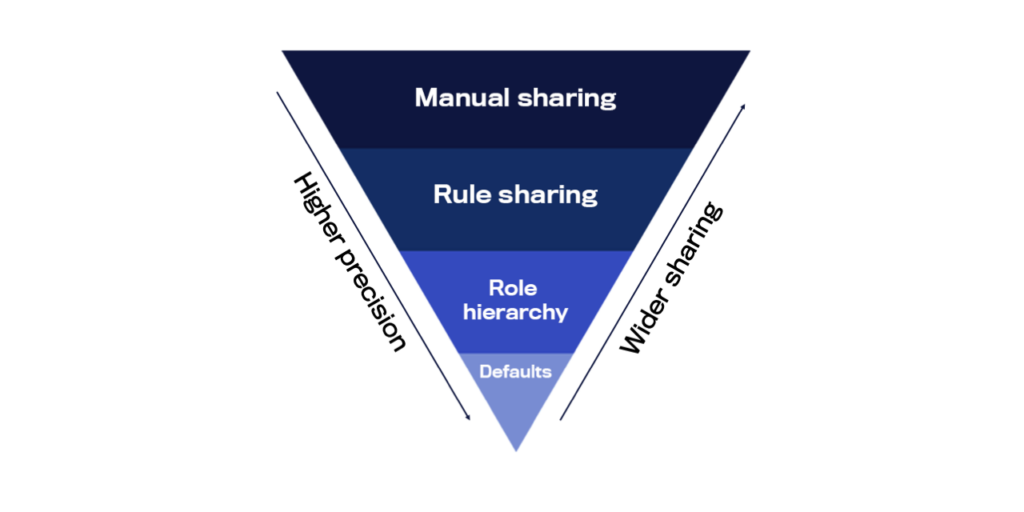
Record level deals with access to individual entries within an object. Salesforce offers several mechanisms to manage this, such as:
- Organization-wide defaults: Set baseline access levels for all records within the organization.
- Role hierarchy: Enables users higher in the hierarchy to access records below them.
- Sharing rules and manual sharing: Facilitate lateral sharing within teams or direct sharing for specific records, ensuring collaboration without compromising security.
External access and advanced cyber security measures on Salesforce
While internal user permissions and sharing rules are critical, Salesforce administrators must also safeguard against external threats. These threats can arise from interactions with Salesforce solutions like Salesforce Experience Cloud, or through third-party applications connected via APIs. Salesforce allows the enforcement of permissions for APIs and apps similarly to internal user settings. It’s crucial to configure these permissions with the strictest settings possible to minimize vulnerabilities and prevent unauthorized access.
Keep your data safe with Salesforce Shield and WithSecure™ Cloud Protection for Salesforce
Even the most robust endpoint security strategies cannot guarantee complete immunity from sophisticated cyber threats. Criminals targeting your organization might mimic legitimate access – also on Salesforce. Salesforce Shield plays a pivotal role here by enhancing file encryption, adding a critical layer of security for data uploaded to the cloud, making it more resistant to unauthorized exploitation.
WithSecure™ Cloud Protection for Salesforce takes security against external threats a step further by providing real-time defense against viruses, malware, ransomware, and phishing threats. It scans all content from files to URLs as it is uploaded to Salesforce, both at the time of upload and whenever a user interacts with the content. This proactive approach not only detects and blocks known threats such as commodity malware, but also uses advanced behavioral analysis to thwart zero-day attacks and emerging threats.
Last piece of advice: secure every access point
For enterprises utilizing Salesforce, protecting every point of access and every point of data interaction – both internal and external – is critical. WithSecure™ Cloud Protection for Salesforce complements Salesforce’s built-in capabilities and Salesforce Shield by offering an additional layer of real-time, proactive protection, ensuring your Salesforce environment remains secure against advanced cyber threats. This dual approach fortifies your cloud data against both conventional risks and sophisticated cyber attacks, whether they are coming through a customer support email, web form or your community portal. Your end-users are secured whether they use a laptop or a mobile device.
For more information on optimizing your Salesforce security against modern cyber threats, get our free security tips ebook or conduct a free risk assessment (we promise it only takes a few minutes and requires no access to your Salesforce orgs).

