-
Salesforce attacks in 2025: Why cyber criminals are targeting Salesforce
Malicious activity targeting Salesforce has increased significantly in the beginning of 2025. Attackers are abusing identity, trust, and business workflows. This blog explores real-world breaches and evolving tactics.
-
Agentforce security: AI agents in Salesforce are fast. Cyber threats are faster.
As AI agents handle vast amounts of data, security risks also increase – malicious files and URLs can introduce malware and phishing threats. To fully and securely unlock Agentforce’s potential, organizations must ensure AI agents operate…
-
Reverse engineering a pain point: How field uploads exposed a hidden threat in Salesforce
A simple question—“Are our field uploads putting us at risk?”—led one manufacturing firm to rethink how they secure Salesforce. In this post, let’s see how mobile workflows uncovered a hidden threat, and how a native,…
-
Coinbase breach: What happened, and what it means for Salesforce security
Coinbase, one of the world’s largest cryptocurrency exchanges, disclosed a data breach that involved the theft of sensitive customer information and a $20 million extortion attempt by cybercriminals. Read more to find out how that…
-
Credential theft, malware, and the hidden risk to Salesforce environments
A large-scale malware campaign exposed how easily stolen credentials can compromise cloud platforms. Here’s why Salesforce environments are vulnerable—and what you can do to protect yours.
-
Salesforce security: What you REALLY need to know
Salesforce security isn’t just IT’s job. Learn how to build resilience, manage AI risks, and close gaps in your shared security model.
-
Securing the future of Agentforce: Why Salesforce data governance can’t be an afterthought
As Agentforce and other AI tools revolutionize customer engagement, I’m seeing a common pattern in the Salesforce ecosystem: companies racing to deploy exciting new tech without fully understanding the risks.
-
How to block encrypted ZIP threats in Salesforce
Attackers exploit password-protected ZIPs to bypass file scanners and slip malware past defenses. Learn how treating encrypted files as policy violations and blocking them directly on Salesforce can neutralize threats before they reach users or…
-
What you need to consider in your file security solution for Salesforce
File uploads in Salesforce are a convenient vector for cyber threats. So, what to look for in a Salesforce file security solution? Let’s mirror industry standards like AV-TEST, and conclude why multi-layered real-time protection is…
-
Jira credentials breached: Why the HELLCAT attacks should alarm every Salesforce customer
The HELLCAT breaches show how a single compromised credential from an old external Jira user can trigger a cascade of damage. Identity security isn’t new, but today’s threats easily bypass traditional defenses. This isn’t just…
-
Future of Agentforce: cyber threat landscape
As organizations integrate AI-driven innovations like Salesforce’s Agentforce, both the operational landscape and threat landscape are changing.
-
What’s new in WithSecure™ Cloud Protection for Salesforce 2.6
Detect malware inside password protected archives and block newly registered – and often malicious – domains
-
The risk of newly registered domains on Salesforce and how to mitigate it
Cyber criminals frequently employ newly registered domains (NRDs) to orchestrate phishing attacks, setting up these domains specifically to host phishing sites that deceive users into divulging sensitive information and account credentials. Beyond phishing, these NRDs…
-
Is your Salesforce DORA compliant?
If you work for a financial institution and European Union regulations apply to your team, you may have bumped into The Digital Operational Resilience Act (DORA). Let’s explore what DORA is and what it means…
-
5 Things You Should Know About Securing Salesforce
Securing your Salesforce instance should be a top priority. But having it be a priority and knowing what to do about it are two different topics. It is a complex topic, but the following “5…
-
Lessons learned from email for Salesforce security
As email is getting stronger and stronger cyber security measures, cyber criminals are seeking new vulnerable avenues to exploit. This shift highlights a crucial lesson for Salesforce security.
-
QR code quishing attacks on Salesforce and how to detect them
QR codes are no stranger in our daily transactions. Originally designed to streamline processes, they have also become a tool for cybercriminals, giving rise to a modern form of phishing called quishing.
-
Q3 2024 cyber threat landscape: Implications for Salesforce security
Understanding the cyber threat landscape is crucial for every cyber defender. Read on to explore the latest trends, such as the tactics, techniques, and procedures (TTPs) used by cybercriminals.
-
WithSecure™ Cloud Protection for Salesforce at Dreamforce 2024
We showcased new product features and customer success stories at booth 2005.
-
What’s new in WithSecure™ Cloud Protection for Salesforce 2.5
Detect and block malicious URLs in your Salesforce environment across custom objects and fields and prevent QR code quishing attacks
-
What’s really happening in your Salesforce environment?
Salesforce’s flexibility brings unique security challenges. Discover why traditional defenses fall short and how to protect your environment from hidden threats.
-
5 steps to a secure Salesforce
Your Salesforce data is under threat. If that data is left unprotected, your business and your customer data could be hit by a ransomware or phishing attack. By default, the infrastructure of Salesforce is secure…
-
The hidden risks of Salesforce—and how to address them
Do you really know what’s happening in your Salesforce environment? Working in enterprise cloud applications like Salesforce is secure—but only up to a point. While software-as-a-service (SaaS) vendors such as Salesforce regularly strengthen their services…
-
Salesforce data residency best practices
In this article, we’ll explore why data residency matters for Salesforce security and provide best practices for managing Salesforce data residency.
-
Salesforce data protection 101 – What is the Salesforce security model?
We know that cyber security is complex. Likewise, your Salesforce environment is no different. Let’s keep things simple in this article, and crystallize what every Salesforce professional should know about Salesforce data protection.
-
What does Snowflake breach mean for Salesforce security?
A recent cyberattack on Snowflake, a cloud-based data warehousing platform, highlights the importance of robust security measures in cloud services. The breach, which involved the exploitation of infostealer malware and stolen login credentials, resulted in…
-
Data residency for Australia & Singapore
In a move that is welcomed by clients throughout South-East Asia and beyond, WithSecure’s Cloud Protection for Salesforce cloud security software now offers data residency capabilities in Australia and Singapore. This native cloud security solution…
-
The Rising Threat of AI-Powered Cybercrime: FraudGPT
As the world increasingly embraces Artificial Intelligence (AI), cybercriminals are also harnessing its power to create sophisticated cybercrime tools. The latest and most alarming development in this realm is the emergence of a new AI…
-
PDF malware and how to defend your Salesforce against it
Envision your Salesforce system as the heartbeat of your enterprise, where every transaction fuels your business growth. Now picture that one seemingly innocuous PDF could undermine it all. This isn’t fearmongering; a research has found…
-
Salesforce data compliance lessons from Australia and Singapore
We have received customer requirements to give customers more control over their security data, especially from Salesforce customers in Australia and Singapore. In this article, we’ll discuss where these trends stem from, and what we…
-
Securing Salesforce Service Cloud
Salesforce Service Cloud is a vital tool for customer service, but its data-rich environment also attracts cybercriminals. Protecting against malware and phishing attacks in Salesforce is essential for maintaining a healthy, secure environment.
-
Using Salesforce securely
The National Cyber Security Centre (NCSC) exists to help make the UK the safest place to live and work online. This month, the NCSC has published new guidance on how to use a cloud service…
-
Countering the risks of file-type spoofing in cybersecurity
Cyber attackers constantly develop new methods to breach systems. A common but often overlooked tactic is altering file extensions to hide malicious files in plain sight: a method called file type spoofing. This article examines…
-
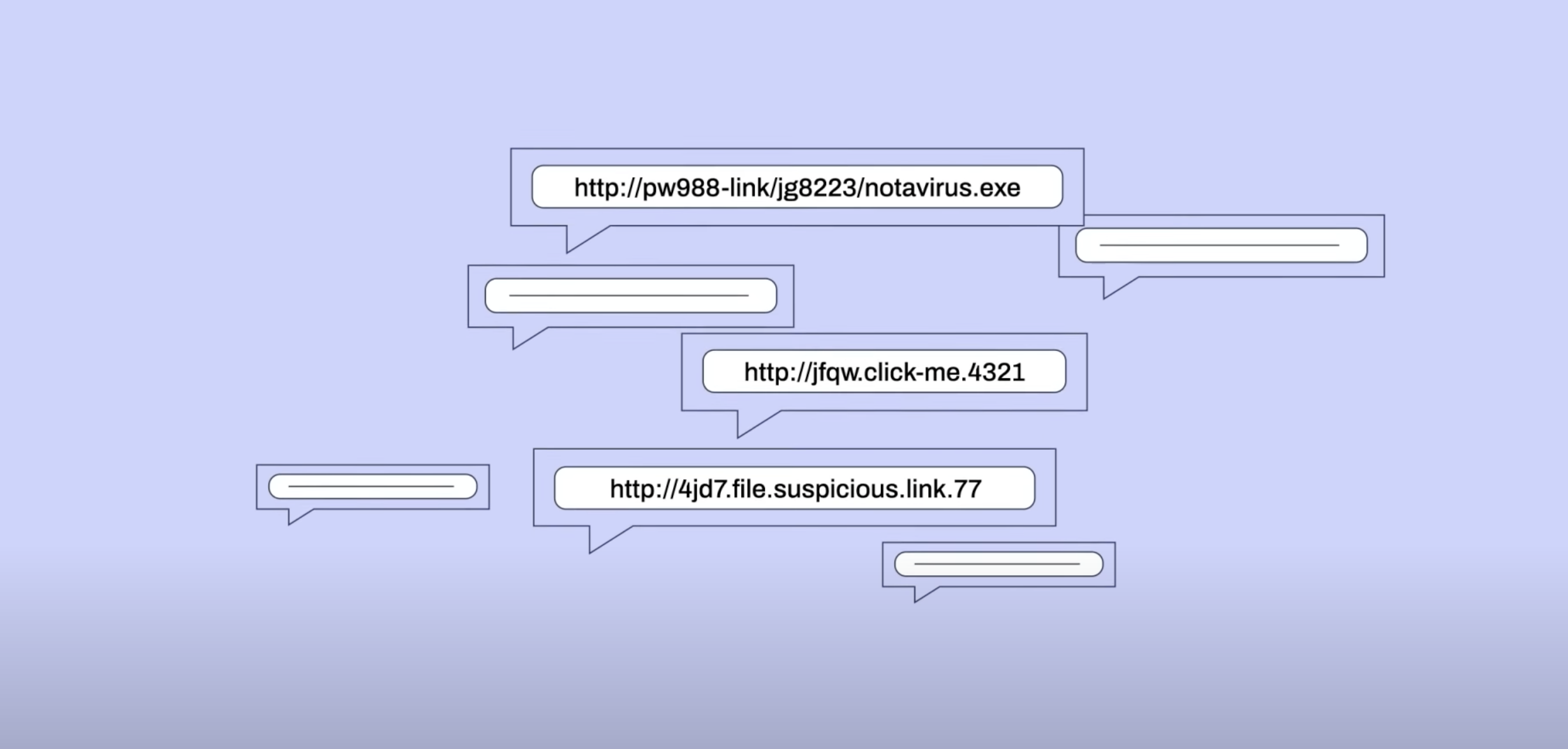
Short links: a hidden risk in your Salesforce environment
Shortened URLs are a staple in our digital lives, especially on social media. They are practical, space-saving tools in character-limited posts, allowing for more informative or engaging content. However, they come with a caveat: the…
-
Protect Salesforce from file-based URL threats
File-based threats are not just about malware; malicious URLs from seemingly innocent files can cause significant damage. It’s time to bolster your defenses and ensure your Salesforce security strategy is airtight against sophisticated URL-based attacks.
-
The “PhishForce” exploit: Cloud vulnerability case study
A look at how attackers used Salesforce’s email features for phishing — and what it tells us about securing cloud platforms.
-
Defending Salesforce against relentless AI-based cyberattacks
Cyber attackers have stepped up their game continuously, and they’re now using artificial intelligence, automation and other advanced technologies to launch increasingly sophisticated, and often AI-based, cyberattacks.
-
Salesforce Security Essentials – 7 Things to Keep in Mind
Salesforce is the leading CRM system in the world and Salesforce Cloud applications such as Sales Cloud, Service Cloud, Experience Cloud, and Community Cloud are now a business-critical service for organizations across a wide range…
-
What are the real risks of using Salesforce?
For businesses, cyber security is a shared responsibility. Like many software-as-a-service (SaaS) providers, Salesforce builds excellent infrastructure security into its products and services.
-
Saleforce security best practices for financial services
Banks and financial institutions are increasingly turning to Salesforce to improve communications with customers and partners.
-
Defending Salesforce against relentless cyberattacks with AI
Salesforce is one of the most popular customer relationship management (CRM) platforms in the world, enabling businesses to manage their customer data, sales activities, and marketing campaigns from a single platform.
-
The role of AI in the modern cyber security landscape
The rise of cyber attacks in recent years has made cyber security an essential aspect of running any business.
-
Is Your Company’s CRM Platform Secure?
Organizations depend on customer relationship management (CRM) systems to build meaningful customer relationships, find new customers, and increase revenues.
-
Why Salesforce cyber security matters
Businesses rely on customer relationship management (CRM) platforms to manage and track their sales and customer data. Salesforce, the world’s leading CRM platform, saves companies millions in overhead costs and, in the process, stores gigabytes…
-
Defending Salesforce from phishing attacks
Millions of users access Salesforce daily to manage company data and information. Unfortunately, this popularity comes with the cost of making the platform an attractive target for malicious actors, including cyber criminals who use phishing…
-
Salesforce phishing scams: What to do when attacked
Phishing is an increasingly popular form of cyber-attack where criminals send messages or emails containing malicious links to trick people into downloading malware or rerouting to fake sites.
-
Cybersecurity Trends and Threats for 2023
Despite global efforts to thwart cyberattacks, the reality is that the number of new threats security teams must deal with grows by the year.
-
Mastering data & security literacy for Salesforce users
It’s more important than ever to ensure your organization is on the right track in terms of data and security literacy.
-
Cyber security skills – efficiency through automation
In the fast-paced world of technology, the importance of cyber security cannot be overstated. As we move into 2023, the skills required to perform effectively in this field have evolved. To begin with, an in-depth…
-
Shared responsibility model: know & reduce your risks
The shared responsibility model (SRM) in cloud security is a crucial concept that both cloud service providers and cloud users need to understand and adhere to in order to minimize the risks associated with cyber…
-
Cybersecurity goes beyond just endpoint protection
Cybersecurity isn’t just about protecting endpoints anymore. With cloud platforms playing a central role in business, organizations need to address growing risks beyond the device level.
-
Understanding the motives and methods of cybercriminals
The computer technology that surrounds us — the devices and software we use every day, as well as the systems upon which our businesses rely — has made cybersecurity an ever-present concern.
-
Understanding internal & external cyber security threats
In today’s rapidly evolving digital landscape, the frequency and sophistication of cyber attacks continue to rise which poses a significant risk to organizations of all sizes.
-
Salesforce security with Kill Chain & MITRE ATT&CK
In today’s digital world, security is a top priority for businesses and individuals alike.
-
Disrupt the kill chain & stop email-to-case attacks
In the world of cybersecurity, organizations must stay vigilant against a myriad of evolving threats. And with Salesforce being a vital platform for businesses worldwide, safeguarding its infrastructure is of paramount importance. One tool that…
-
Disrupt the kill chain & stop community portal attacks
In today’s digital age, businesses are heavily reliant on cloud-based technology, with Salesforce being one of the most popular CRM platforms in use. While Salesforce has a built-in security mechanism to protect customers from cyberattacks,…
-
Secure architecture for Salesforce Experience Cloud
Experience Cloud is an incredible tool capable of creating and extending the customer experience of those who leverage it. When building an Experience Cloud site, what should security-conscious architects and admins be thinking about from…
-
Securing Experience Cloud at scale
Security leaders share how they navigate the risks of Salesforce Experience Cloud—from guest user access to integration threats—and what it takes to secure it in enterprise environments.
-
Disabling vs. securing file upload on Salesforce
Salesforce provides various ways for users to add file attachments, consolidating documents related to leads, cases, and more. File uploads offer numerous beneficial use cases, yet they are not without associated risks.
-
How to make sure your next Salesforce project is secure
Salesforce is designed to be highly customizable to meet your business needs. There are more than 3,400 applications on the Salesforce AppExchange alone, and many third-party APIs and plugins are readily available online.
-
Compromised DevOps tools in supply chain attacks
Here, we’re focusing on how supply chain tactics can be used to exploit Salesforce platform through compromised DevOps tools, that is one of the most overlooked threats in digital supply chains. As a critical part…
-
Third-party integrations: Hidden Salesforce risks
Supply chain attacks have emerged as one of the greatest security threats in recent years. Gartner has named digital supply chain risk as one of the leading security and risk management trends for 2022 and…
-
Protecting Salesforce from human error
When using Salesforce, companies need to bear in mind a variety of different risk factors.
-
Think your Salesforce data is secure? Think again.
Salesforce operates a shared security model. This means you are responsible for protecting your business data—and keeping harmful content such as files, phishing emails, and rogue links out of your CRM, and your wider business…
-
Disrupting the Kill Chain with WithSecure™ Cloud Protection for Salesforce
Salesforce Cloud applications like Sales Cloud, Service Cloud or Experience Cloud are now a business-critical service for organizations across a wide range of industries and verticals. Unfortunately, their popularity has attracted the attention of cyber…
-
Cyber Kill Chain
Learn how cyber attackers can leverage vulnerabilities in Salesforce and how you can stop them.
-
Why CASB might not be the right fit for securing your Salesforce
CASBs help enforce cloud policies, but they’re not built for Salesforce. Discover where they fall short — and how native protection closes the gap.
-
Anatomy of a Salesforce supply chain attack
Every modern enterprise today sits at the center of a vast and complex network of digital suppliers. Affordable high-speed internet and the vast and fast-growing global cloud market mean that organizations can easily outsource anything…
-
What’s new in WithSecure™ Cloud Protection for Salesforce 2.4
Detect and block malicious URLs in your Salesforce environment, from custom objects and fields to file attachments and even shortened web links.
-
What’s new in WithSecure™ Cloud Protection for Salesforce 2.3
Detect and block disguised file types, and report detections straight from the app
-
What’s new in WithSecure™ Cloud Protection for Salesforce 2.2
Master your data: deep threat analysis meets controlled geographic processing
-
What’s new in WithSecure™ Cloud Protection for Salesforce 2.1
Understand your security status and configurations with a glance
-
What’s new in WithSecure™ Cloud Protection for Salesforce 2.0
Configurable Click-Time URL Protection, bolstered file scanning, future-proof solution architecture and more
BOOK A DEMO
Secure your Salesforce today
Tailored for high compliance sectors, our certified solution safeguards Salesforce clouds for global enterprises, including finance, healthcare, and the public sector.
Fill the form and get:
Free 15-day trial
Personalized Salesforce security risk assessment report
Demo and a solution consultation
Support from our experts with setup and configurations