Digital supply chain attacks are a leading cyber threat today, and it’s believed the number of attacks tripled in 2021 alone. Some of the biggest data breaches of the last year have centered on digital supply chains.
Here, we’re focusing on how supply chain tactics can be used to exploit Salesforce platform through compromised DevOps tools, that is one of the most overlooked threats in digital supply chains. As a critical part of thousands of organizations’ customer relationship infrastructures, Salesforce cloud is one of the attractive targets for threat actors seeking access to sensitive data.
Developers have a large number of tools at their disposal, and there is a tendency to blindly trust they are secure, particularly if they come from a known vendor or official store. But as the infamous SolarWinds hack shows, even well-known vendors can be compromised and used to enable an attack.
Compromised DevOps tools can be used to facilitate attacks on any IT ecosystem the developer is working on, such as Salesforce platform.
Watch this short dynamic video to see a supply chain attack via DevOps tools and Salesforce platform at work.
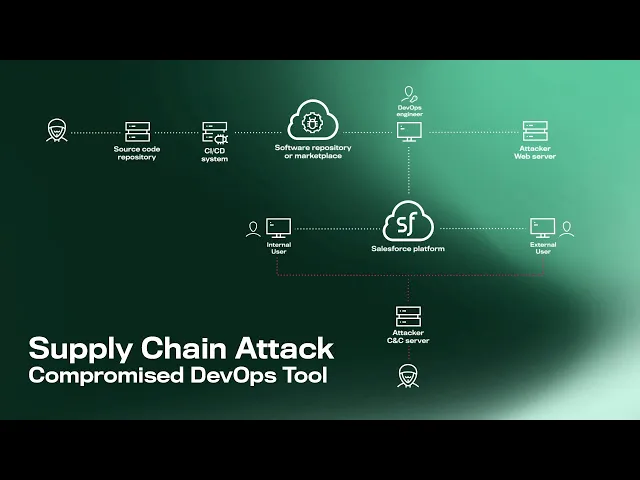
Such attacks may begin with the adversary sniffing out poorly managed source code repositories. Scanning unsecured public source codes can reveal user credentials or API tokens, which can be used to gain access to, for example, the CI/CD tool used by a software development company offering their application via software repository or marketplace.
From here, bad actors can covertly inject malware into a software built by the CI/CD tool before it is published to the marketplace. Now, any users downloading the software will receive a compromised version containing a nasty hidden surprise.
The hidden payload will download additional malware from the attacker’s web server, enabling them to compromise both the user’s endpoint machine, and any on-prem or cloud-based systems they are connected to. This can be Salesforce platform that allows to install or connect third party applications.
The attacker can now exploit all of Salesforce’s connections and capabilities, such as using its content sharing functionality to distribute specifically crafted malware or phishing links to users, including employees, partners, and customers.
Now they can perform any number of malicious activities, with one of the most common outcomes being the establishment of a command and control (C&C) backdoor that will allow them to continuously achieve lateral movement and begin stealing critical data.
BOOK A DEMO
Secure your Salesforce today
Tailored for high compliance sectors, our certified solution safeguards Salesforce clouds for global enterprises, including finance, healthcare, and the public sector.
Fill the form and get:
Free 15-day trial
Personalized Salesforce security risk assessment report
Demo and a solution consultation
Support from our experts with setup and configurations
