Your data, your problem: Your responsibility for securing Salesforce
To understand this risk, you need to understand how Salesforce security works and what all users need to take responsibility for. Salesforce has solid infrastructure security in place, but not all security areas are the cloud vendor’s responsibility, and are therefore not covered by the platform’s built-in capabilities. And care is needed: during 2023, WithSecure detected over a 700% increase in malicious files and URLs on Salesforce through monitoring.
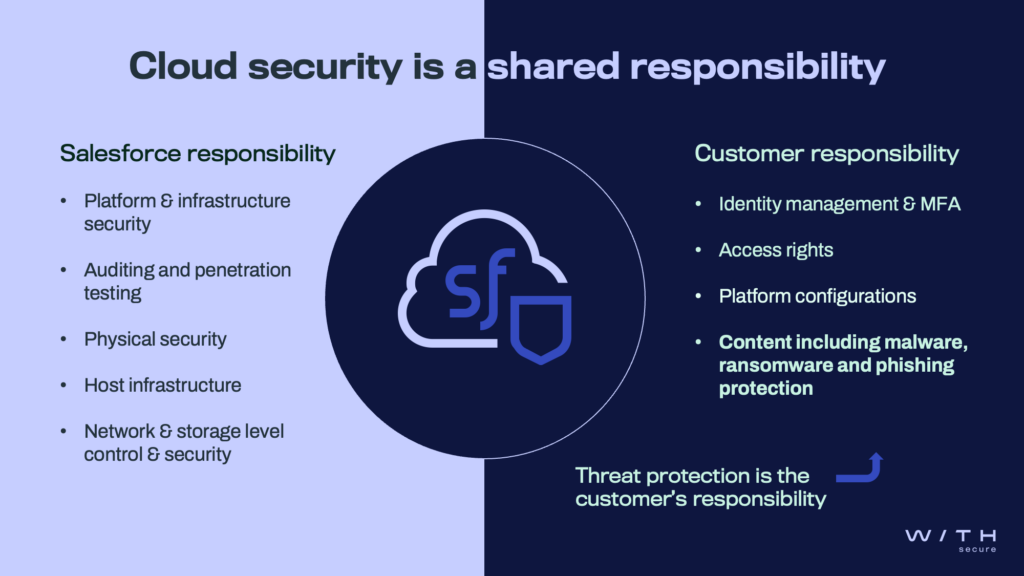
A shared responsibility for security
Like most SaaS vendors, Salesforce uses the shared responsibility model for securing its platform. The principle is simple: the responsibility for securing Salesforce is shared between the vendor and the user. Salesforce is responsible for the security of the cloud service infrastructure, which includes the servers, compute, storage, and networks.
Your part of the bargain is to take ownership of securing the activity that takes place in the cloud. In practice, securing the data you input and manage is up to you. That means securing the files, links, text, and other content collected by Salesforce-generated forms and websites. This content is typically created and submitted by your customers or your partners.
However, too many enterprises assume their activities and data are secure, failing to realize that Salesforce does not scan documents, files, URLs, or QR codes for viruses or malware. But this is not the case. In reality, Salesforce users are increasingly falling prey to cyber criminals who are using implementations of the platform to piggyback malicious files and links into corporate networks.
Importance of file and URL scanning
Salesforce is a treasure trove of valuable data and highly connected both inside and outside the customer organization. Because of this, cyber criminals find Salesforce an attractive entry-way to launch phishing attacks and complex supply-chain attacks. These malicious actors exploit the platform to disseminate malware and execute phishing attacks, leveraging both files and URLs as vectors.
Deloitte reports that 2 in 5 cyber attacks involve phishing. In 2023, WithSecure detected a 700% increase in malicious files and URLs within Salesforce environments, underscoring the escalating cyber risk. If you don’t think you have a Salesforce security problem, then you do have a problem.
Traditional security methods fall short
The security measures provided by many enterprises, such as email and network monitoring, do not extend to customer-facing platforms like Salesforce. This disconnect allows cybercriminals to embed malicious files and links directly into Salesforce, bypassing conventional security measures and directly threatening corporate networks.
The result is that criminals can compromise a network by uploading phishing links and malware into:
- Partner and community portals
- Customer-facing websites
- Forms
- Chats
- Support emails
Because these are not scanned by the traditional solutions, malicious files and links can be opened by unsuspecting end-users and put customer and other sensitive data at risk. The results can be data loss, operational disruption, loss of sales revenue due to suspended campaign activity, fines for failing to meet industry compliance standards, loss of trust, and reputational damage. Customers naturally place a high value on the privacy of their data. Once that’s lost, trust is hard to rebuild.
Securing Salesforce in seconds
Taking action is easier than you think. Salesforce allows business users to easily engage with prospects and customers and experiment with new ideas. Engaging with the technical or security team around securing your Salesforce environment at an early stage, fostering good lines of communication, and developing safe security practices now will save pain and cost in the future.
WithSecure™ Cloud Protection for Salesforce offers a tailored security solution designed in collaboration with Salesforce. This application delivers real-time threat protection, scanning and neutralizing threats such as malicious URLs and files within Salesforce. The advanced threat protection mechanisms, including AI and cloud sandboxing, enhance security without disrupting user experience.
WithSecure™ has recently introduced new capabilities to protect against QR code-based phishing attacks, detect malicious URLs hidden inside files, block shortened URL threats, and block newly registered domains – providing a comprehensive security layer that adapts to the complex threat landscape. Get constant clarity of your content security status and see what is happening in real time.
The bespoke solution is designed with Salesforce and can be deployed in minutes, providing instant protection and security visibility.
How does Salesforce handle security, and what are my responsibilities?
Salesforce adheres to the Shared Responsibility Model (SRM), where it secures its infrastructure and offers additional security services. Salesforce’s own security solutions like Salesforce Shield and Salesforce Data Mask are supportive but don’t cover malware and phishing detection. However, customers must protect their data, configure access controls, and secure Salesforce objects. Importantly, Salesforce does not provide malware, ransomware, or phishing link detection, urging customers to partner with vendors like WithSecure for comprehensive protection.
Why do I need advanced threat protection if Salesforce already has security capabilities?
Salesforce provides robust infrastructure security; however, as the data owner, you’re responsible for securing your data within the platform. WithSecure Cloud Protection for Salesforce seamlessly complements Salesforce’s native security features, enhancing your ability to comply with security responsibilities and providing crucial visibility into cyber threats, significantly reducing incident response costs.
Is URL-based threat detection necessary on Salesforce?
Absolutely. Our findings show that URL-based threats are extremely prevalent in Salesforce environments. Majority of cyberattacks involve phishing, which often utilizes URLs. These attacks are increasingly common on Salesforce, a platform where users may not be as vigilant against phishing as they are with email, raising the risk of human error. URLs have become significant threat vectors, with WithSecure, identifying about 1.5% as malicious – a figure unfortunately expected to increase.
How can I see WithSecure Cloud Protection for Salesforce in action?
Explore WithSecure Cloud Protection for Salesforce on Salesforce AppExchange, where you can read user reviews and take a test drive. Additionally, book a demo to see live how it can fortify your Salesforce environment against cyber threats.
Where can I find user reviews?
You can find customer reviews of WithSecure™ Cloud Protection for Salesforce on Salesforce’s AppExchange market place. You can also check out our customer references. Salesforce Ben has also reviewed the solution thoroughly. Salesforce file scanning capabilities use the same anti-malware engines as WithSecure™ endpoint security solutions, which have achieved 100% effectiveness in detecting both commodity and zero-day malware in AV-TEST Institute’s independent evaluations.
Let’s get in touch. Don’t let one malicious file disrupt your business.
If you want to learn more about WithSecure™ Cloud Protection for Salesforce, reach out for a conversation, we’d love to talk with you about your current Salesforce risks and how we can help you manage them.
Don’t let one malicious file disrupt your business.
BOOK A DEMO
Secure your Salesforce today
Tailored for high compliance sectors, our certified solution safeguards Salesforce clouds for global enterprises, including finance, healthcare, and the public sector.
Fill the form and get:
Free 15-day trial
Personalized Salesforce security risk assessment report
Demo and a solution consultation
Support from our experts with setup and configurations