This time our threat landscape focus is on ransomware and its implications for cloud services, specifically Salesforce. With attackers increasingly targeting cloud services and public-facing apps, and a 366% increase in malicious file detections on Salesforce in Q2 2024 compared to Q2 2023, ransomware is not a threat to be taken lightly in any Salesforce security strategy.
Cyber threat landscape shifts toward cloud and SaaS exploitation
Cyber threat landscape is seeing an increased focus on the cloud. Attackers have recently leveraged legitimate file transfer and cloud services to facilitate their operations more and more. These services offer a low-key and cost-effective infrastructure which tends not to trigger security alerts as some more traditional methods might.
Symantec’s Threat Hunter Team has recently identified three new espionage operations utilizing cloud services and has uncovered additional malicious tools in development:
- GoGra (Trojan.Gogra): Targets a South Asian media organization using Microsoft’s Graph API for C&C communications via email, encrypting messages with AES-256. Developed in Go, active since November 2023.
- Firefly Tool: Used by the Firefly group to exfiltrate data from a Southeast Asian military organization. It searches for and uploads .jpg files (actually encrypted RARs) from System32, using Google Drive.
- Trojan.Grager: Targets entities in Taiwan, Hong Kong, and Vietnam, using Microsoft’s Graph API via OneDrive for C&C. Distributed through a Trojanized 7-Zip installer, linked to the UNC5330 group.
- MoonTag: A developing backdoor associated with a Chinese-speaking actor, noted for its use of the Graph API and discussed in a Google Group.
Salesforce and SaaS applications are targets of UNC3944 threat group
Salesforce and SaaS are becoming more prevalent in the threat landscape. Google Threat Intelligence has observed the activities of UNC3944, a financially motivated threat group that has been active since at least May 2022, and has recently targeted SaaS applications. Initially focused on credential harvesting and SIM swapping, UNC3944 has since shifted to primarily conducting data theft extortion, expanding their target industries and utilizing fearmongering tactics for access. They’ve adapted their methods to include theft from SaaS applications to attacker-owned cloud storage and have employed various advanced techniques to facilitate their attacks.
UNC3944 accessed Salesforce among other SaaS applications using stolen credentials facilitated by single sign-on systems. They conducted reconnaissance within these platforms, likely targeting data for exfiltration, and using third-party cloud synchronization tools like Airbyte and Fivetran to transfer data to external cloud storage.
Key Tactics, Techniques, and Procedures (TTPs) of UNC3944:
- Social engineering: They have successfully manipulated corporate help desks using victims’ personal information to gain access to privileged accounts and bypass multi-factor authentication (MFA).
- Abuse of SaaS permissions: UNC3944 exploited permissions in applications like Okta to broaden their access within targets’ systems, encompassing both on-premises infrastructure and cloud-based applications.
- Virtual machine compromise: The group has created new virtual machines using administrative privileges obtained through SSO applications, using them for subsequent malicious activities and to bypass traditional security controls.
The use of cloud services by attackers is becoming a preferred method for maintaining stealth and managing cost-effective operations. The attackers are learning from each other, adopting successful techniques across various espionage and cybercriminal groups. Extensive coverage of cloud and SaaS environments in security strategies has never been more critical.
Disney moves away from Slack after a data breach of 1 TB – likely caused by a human error
In a major data breach, Disney experienced a significant compromise of corporate data, possibly due to vulnerabilities on an employee’s personal gaming computer. This breach led to the downloading of over 1TB of data through Slack, which resulted in the suspension of the platform for internal communications.
Our team doesn’t have the forensics data of the case, but some experts claim that the breach was not a direct result of flaws in Disney’s or Slack’s systems. Instead, it allegedly occurred because an employee inadvertently installed a malware-infected game modification. This malware, an Information Stealer, captured credentials and accessed Slack, where it exploited the employee’s compromised computer. The lack of Multi-Factor Authentication (MFA) on the password vault allowed attackers to access vast amounts of sensitive data easily.
Some experts suspect that the attackers were helped by an insider, and others that the breach was a result of a general lack of defensive mechanisms at Disney’s end.
A teenager leveraged Slack and stole details about unreleased GTA 6 from the gaming company Rockstar in 2022. The attacker was sentenced to life.
In 2023, another threat actor exploited access to Slack channels to initiate a malware attack on MGM Resorts, a major global casino and resort.
Almost half of ServiceNow KB instances leak sensitive data
A study by AppOmni revealed that over the past year nearly 45% of ServiceNow Knowledge Base (KB) instances were leaking sensitive data, including personal identifiers, internal system details, and live system credentials. The culprit of these breaches were outdated or misconfigured access controls. This is possibly due to widespread misunderstanding of KB access controls or replicating misconfigurations across instances.
Despite ServiceNow’s 2023 security updates aimed at restricting unauthenticated data access, many of these updates were ineffective for KBs, which often contain highly sensitive internal data. The company has responded by collaborating with customers so that KB access control misconfigurations are fixed.
Lockbit ransomware group is down but not out
The Lockbit ransomware group, once among the most active, has seen a significant decline in its operations following targeted law enforcement actions from the U.S. Department of Justice, Federal Bureau of Investigation, the United Kingdom’s National Crime Agency, the Australian Federal Police, among other international partners.
The disruption has led to a sharp decrease in the number of victims, with reported cases falling to single digits. Despite these setbacks, there have been notable attempts to revamp their operations. For example. they have made experimental changes to their data leak sites (DLS) and updates to their DDoS protections. These maneuvers suggest a strategic recalibration aimed at evading detection and sustaining their criminal activities.
Despite significant law enforcement interventions, the Lockbit group’s ability to adapt and attempt to rebuild its infrastructure is indicative of the resilience and persistence of modern ransomware operations. These groups are quick to learn from interventions, often emerging more sophisticated and harder to combat.
Ransomware-as-a-Service is the business model of cyber crime in 2024
The disruption on major ransomware groups has led to a reshuffling of ransomware affiliates, gravitating towards established Ransomware-as-a-Service (RaaS) networks. RaaS is a subscription-based model that enables affiliates to use pre-developed ransomware tools to execute cyberattacks. Similar to software-as-a-service (SaaS) offerings, RaaS providers offer their malicious software on a rental or commission basis, providing updates and support.
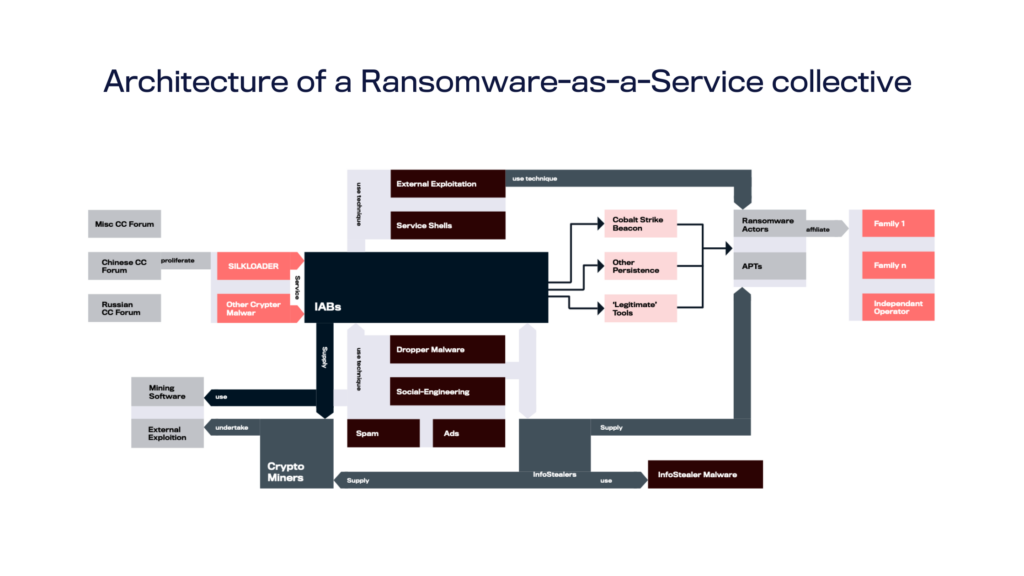
All in all, the professionalization of ransomware operations through RaaS models presents new challenges for cybersecurity defenses. These models facilitate a lower barrier to entry for inexperienced cybercriminals and enable rapid scaling of operations. The attraction of RaaS platforms has flooded in new ransomware variants, correspondingly calling for layered defense strategies.
New threats on the block: new groups form as old dismantle
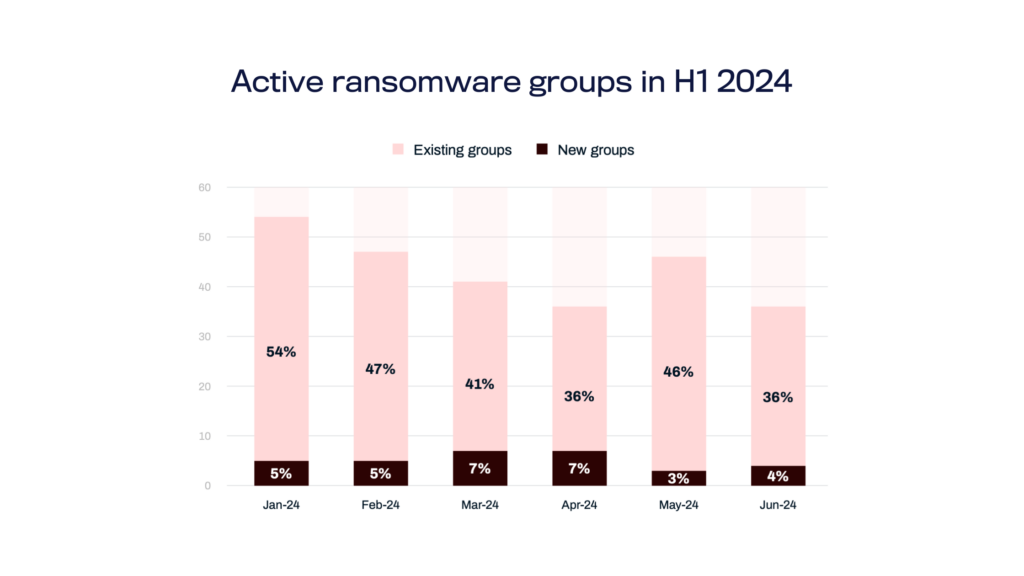
Our research team has also witnessed the rise of new players such as Cicada3301, SenSayQ, and WikiLeaksV2. Each group has demonstrated distinct patterns of targeting and victimology, such as targeting financial software companies and leaking sensitive health sector data. With this in mind, these emerging groups underscore the dynamic nature of the ransomware ecosystem. They continually evolve with new tactics and targets.
The group dynamics are in a constant flux. For example, from the total number of 67 operational ransomware groups our research team has tracked in 2023, 31 have not been operational in Q2 2024. Our team has seen 31 new ransomware groups in 2024. It’s unlikely that many, if any of these projects will survive.
RansomHub’s fast advancement and aggressive affiliate strategy
RansomHub, a new extortion platform operational since early 2024 and believed to be based in Russia, has quickly established itself by offering lucrative terms to affiliates, significantly impacting the ransomware affiliate market. RansomHub is disrupting the RaaS field by letting affiliates accept payment from the victims directly, before sending their share to the RansomHub. What’s more, by allowing affiliates to keep a major portion of the ransom and only taking a small commission, RansomHub has managed to attract experienced groups like ScatteredSpider and members of Lockbit.
RansomHub’s operational capacity, threat level and the number of victims have consequently increased. According to our research team, RansomHub is in fact currently the most active platform observed in the field. In the same fashion, ZeroFox accounts the platform to be responsible for 14.2 % of all cyber attacks in Q3 2024. The majority of victims are in North America (39.4%) and Europe (34.3%). Victims are across diverse sectors, for example manufacturing, retail, healthcare, technology.
At the same time, CISA, along with the FBI, MS-ISAC, and HHS, issued a joint Cybersecurity Advisory on RansomHub Ransomware. This advisory offers network defenders key details such as indicators of compromise (IOCs), tactics, techniques and procedures (TTPs) tied to RansomHub, drawing on findings from recent FBI investigations and third-party reports.
RansomHub has been using sophisticated EDR-killing executable tooling. It disables endpoint detection and response (EDR) software and gains escalated privileges on compromised devices, while designed to bypass several common anti-malware tools. The malware has been found in many formats such as EXEs and PowerShell scripts.
Real-life impacts of ransomware fallouts
Financially driven ransomware attacks can have notoriously severe impacts on victims. Overall, our research team has found that ransom payments and incidents remain higher in the first half of 2024 compared to previous years.
Dark Angels behind a record ransom payment
In early 2024, Zscaler and Chainalysis detected a monumental ransom payment of $75 million directed to a cryptocurrency wallet managed by the Dark Angels ransomware group. The identification of the victim was not disclosed as per standard reporting practices, but it is strongly suggested that the payor was Cencora, a Fortune 50 pharmaceutical company. Why so? Cencora publicly acknowledged a ransomware attack and data theft in February 2024, making them a probable candidate. The company, valued at $10 billion with annual revenues reaching $262 billion in 2023, found the payment necessary to restore operations and prevent further data leaks.
Further investigations reveal that the attack’s ramifications extended beyond Cencora. The company, along with at least two of its subsidiaries, reported stolen data to regulators, implicating a broader network of affected entities. In May, additional disclosures indicated that the data breach had impacted numerous major pharmaceutical companies including Pfizer, Bayer and Novartis, among others. These partners also experienced breaches connected to Cencora’s compromised systems, specifically through the Lash group subsidiary.
The sizable ransom from this single incident highlights Dank Angels’ impact. The strategy employed by Dark Angels suggests a focus on high-value targets – often termed “big game hunting” – which involves fewer, highly profitable attacks rather than numerous smaller-scale ones. It’s difficult to say whether Dark Angels have an intentional strategy of big game hunting, or if they just got lucky.
There were no major outages or operational disruptions reported (at least so far). However, the widespread effects of this attack, involving a network of companies with a combined revenue in the trillions, illustrate the extensive potential for damage and disruption caused by ransomware operations targeting major players in critical industries.
Japanese media giant’s market value plummets in the ransomware attack aftermath
Another example, the ransomware strike on Japanese media company Kadokawa Corporation served as a stark reminder of the broad and enduring impacts such attacks can have on businesses. The assault not only disrupted daily operations but also inflicted severe financial and reputational damage. Prior to the attack in early June, Kadokawa’s market value stood at approximately JP¥465 billion (USD$3 billion). Following the incident, its share price plummeted by 15%. Subsequently, this erased JP¥70 billion (USD$500 million) from its market capitalization. This significant drop in share price, which appears solely attributed to the ransomware attack, underscores the high stakes of cybersecurity in protecting not just operational capabilities but also financial stability and public perception.
Public health at stake
The National Health Laboratory Service (NHLS) of South Africa suffered a ransomware attack on June 22nd. The attack continued to disrupt services into July. This attack has been particularly critical as it hindered access to laboratory test results amid an outbreak of mpox disease. This incident demonstrates how significantly ransomware impacts public health and safety of citizens globally.
To pay or not to pay
Ransomware groups often aim to build trust with victims by promising data recovery upon ransom payment, giving false hopes that this will restore normal operations. Ransomware operators often brand themselves as ‘pentesters’ with the intention to appear professional and reassure victims about data deletion and decryption.
Despite this, the majority of organizations paying ransoms suffer subsequent attacks, often facing even higher demands than before. Cybereason reaserch claims that percentage of victims facing a second attack is as high as 78%.
Ransomware operators are unreliable and their assurances of not targeting victims again should not be trusted. Therefore, paying a ransom based on trust in these actors is not advisable. Acknowledging research that quantifies the deceitfulness of ransomware actors is crucial, as it together with prohibiting legislation significantly influences the ransomware landscape.
Salesforce security implications of the current threat landscape
The emergence of new ransomware groups and the evolving tactics suggest that Salesforce environments are likely to be increasingly targeted as an alternative to traditional and easier to detect vectors. In fact, we’ve detected a 366% increase in malicious files on Salesforce in Q2 2024 compared to Q2 2023.
For Salesforce, it’s important to stay vigilant against ransomware campaigns that leverage Salesforce as a channel for malware delivery or social engineering tactics to lure users to phishing sites. Besides human errors, novel campaigns can target vulnerabilities in cloud environments or through third-party integrations.
Salesforce security recommendations simply put
Constantly transforming threats require a layered and proactive approach to cybersecurity. No silver bullets. Because of that, we’ve compiled a comprehensive list of Salesforce security recommendations in light of recent cyber crime developments:
- Auditing: Activate comprehensive auditing that covers cloud environments including Salesforce to identify and patch security gaps.
- AntiVirus: Threat protection such as WithSecure™ Cloud Protection for Salesforce solutions at the entry-point such as Salesforce together with endpoint security will block the majority of file-based ransomware threats. Make sure that the solution has up-to-date threat intelligence source.
- Employee training and awareness: Social engineering remains a significant threat vector. Training Salesforce users to recognize phishing attempts and other social engineering tactics is critical.
- AntiPhishing: By implementing an antiphishing solution on Salesforce level, you can automatically stop phishing attacks. It’s important to go beyond traditional attack vectors like email.
- Strengthened access controls: Enforce strict conditional access to mitigate credential compromise. Salesforce environments should adopt the principle of least privilege. Routinely audit permissions.
- Third-party risk management: As Salesforce often integrates with numerous third-party applications, ensuring these connections are secure is essential to prevent ransomware spread or data leaks. You should choose security tools based on integration simplicity, preferring native solutions.
- Data management policies: The revelation that Lockbit held onto data it claimed to have deleted is a crucial reminder of the risks involved in data handling and storage. You should implement robust data encryption, regular audits, and follow strict data handling and deletion protocols to minimize potential damage.
- Limit BYOD: The breach of Disney’s Slack data resulted from a malware infection on an employee’s personal device – a reminder to limit allowing personal devices into corporate systems.
- Extortion preparation and response: You should include Salesforce in incident response strategies. This means close collaboration between security and Salesforce teams, having secure and tested Salesforce backups and a clear communication plan for dealing with ransom demands.
References
AppOmni. Enterprise ServiceNow Knowledge Bases at Risk: Extensive Data Exposures Uncovered.
CISA. CISA and Partners Release Advisory on RansomHub Ransomware.
Cybereason. Ransomware: True Cost to Business 2024.
Dark Reading. Thousands of ServiceNow KB Instances Expose Sensitive Corporate Data.
Google. UNC3944 Targets SaaS Applications.
National Crime Agency. The NCA announces the disruption of LockBit with Operation Cronos.
National Crime Agency. International investigation disrupts the world’s most harmful cyber crime group.
NCSC. NCSC and international partners shine a light on Lockbit ransomware threat.
Salesforce. Multi-Factor Authentication for Salesforce Orgs.
Symantec. Cloud Cover: How Malicious Actors Are Leveraging Cloud Services.
The Cyber Express. Data Breach Fallout: Disney Severs Ties after Slack Hack?.
The Hacker News. RansomHub Group Deploys New EDR-Killing Tool in Latest Cyber Attacks.
The Hacker News. RansomHub Ransomware Group Targets 210 Victims Across Critical Sectors.
U.S. Department of Treasury. United States Sanctions Senior Leader of the LockBit Ransomware Group.
WithSecure. Threat Highlights Report June 2024.
WithSecure. Threat Highlights Report July 2024.
WithSecure. Ransomware landscape H1/2024.

