As the saying goes, with great power comes great responsibility, and protecting sensitive data is of utmost importance. The latest Cost of a Data Breach Report published by IBM revealed that the average cost of a data breach is at an all-time high of $4.35 million. And if we look at the U.S. alone, that number goes all the way up to $9.44 million.
In light of these alarming statistics, we’ll take a deep dive into the Cyber Kill Chain and explore how attackers exploit the Salesforce Community Portal to gain unauthorized access. We’ll also discuss how WithSecure’s Cloud Protection for Salesforce can help businesses mitigate these types of attacks and provide insights on how to improve their overall security posture. Let’s begin.
Why Do Criminals Target the Salesforce Community Portal?
Cybercriminals are after two main things: money and data. Exploiting the Salesforce Community Portal allows criminals to gain access to both of these things at once. And it’s not easy, but if they gain access, they can potentially access a treasure trove of data by moving laterally through your network — causing damage as they go. This means that if cybercriminals are able to compromise the Salesforce Community Portal, they may be able to leverage that access to gain control over your other systems and applications.
This information can be used for a range of nefarious activities, such as identity theft, financial fraud and more. Every type of cybercriminal has different motivations and techniques , but the end result is the same. Loss of money, brand reputation and data.
Closing the Gap: Securing the Salesforce Community Portal
While Salesforce offers critical infrastructure-level security measures like replication, backup, disaster recovery, encrypted network services and advanced threat detection, it’s important to note that each individual company is ultimately responsible for securing data and access controls.
One of the most common methods attackers use to gain access to Salesforce is through the Community Portal. In this scenario, the attacker registers and creates a new user account, disguised as a member of your community who would have legitimate access to your Community Portal.
To go into further detail, let’s dissect this external threat using the Cyber Kill Chain. But first, a quick recap:
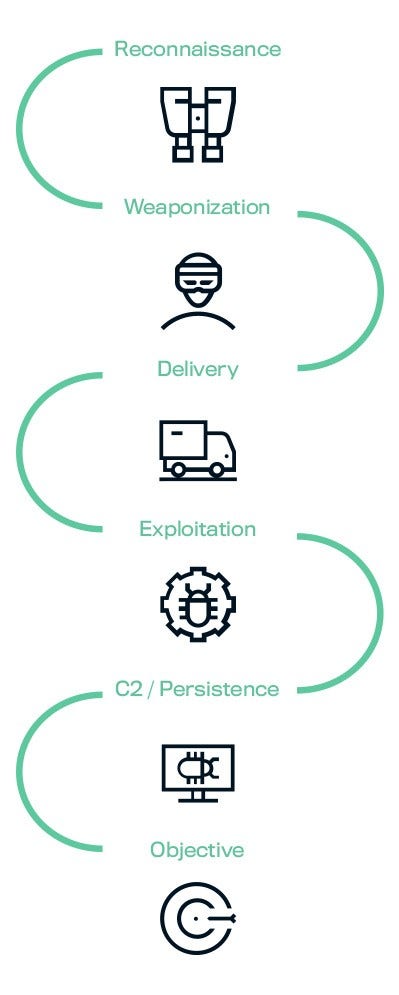
- The Cyber Kill Chain is a widely accepted model that describes the different stages of a cyberattack. The stages include reconnaissance, weaponization, delivery, exploitation, C2/persistence and objective.
Although we’ve outlined a typical attack scenario, there are many other ways in which these attacks could occur. Cyberattacks don’t follow a linear process; attackers can jump between stages, go back and forth and adjust their tactics based on their objectives.
Now that we’re refreshed on the Cyber Kill Chain, let’s take a look at how it applies to this attack.
- Reconnaissance
Once the attacker has created a user account, they perform reconnaissance to gather information about the platform’s vulnerabilities. This may involve searching for outdated software versions, unpatched vulnerabilities or misconfigured settings. - Weaponization
After collecting information about the platform’s vulnerabilities, the attacker creates a weaponized document with a vulnerability exploit. This can be a Word document with malicious macro or a PDF document with embedded JavaScript code. - Delivery
The attacker then uploads the weaponized document to the Community Portal, saved in Salesforce Experience Cloud as a content document or attachment. - Exploitation
An internal user may download and open the file, unknowingly executing the weaponized payload, which exploits the vulnerabilities within the applications on their device. - C2/Persistence
The attacker now has access to the user’s device and can proceed to lateral movement, persistence or further internal reconnaissance. - Objective
The attacker works to remain undetected, maintain persistence and exfiltrate data.
Although we’ve outlined a typical attack scenario, there are many other ways in which these attacks could occur. Cyberattacks don’t follow a linear process; attackers can jump between stages, go back and forth and adjust their tactics based on their objectives.
The Product: WithSecure™ Cloud Protection for Salesforce
One thing is certain: Attackers are relentless, always looking for new ways to exploit vulnerabilities. WithSecure™ Cloud Protection for Salesforce is the ultimate security solution for businesses looking to protect their data against advanced cyberthreats.
The solution offers comprehensive protection against a range of threats, including ransomware, zero-day malware, viruses, trojans and phishing links. Developed in collaboration with Salesforce, WithSecure™ Cloud Protection complements the platform’s native security capabilities, ensuring maximum protection against cyberthreats.
One of the key features of WithSecure™ Cloud Protection is its ability to scan URLs every time they’re clicked. Putting this into context, an attempted attack via the community portal would be effectively stopped at stage four.
It’s also ISO 27001 and ISAE 3000 (SOC 2) certified, giving you greater peace of mind that your data is safe. Don’t let cybercriminals steal your data and compromise your business. Get in touch with us today.
BOOK A DEMO
Secure your Salesforce today
Tailored for high compliance sectors, our certified solution safeguards Salesforce clouds for global enterprises, including finance, healthcare, and the public sector.
Fill the form and get:
Free 15-day trial
Personalized Salesforce security risk assessment report
Demo and a solution consultation
Support from our experts with setup and configurations
