Most companies operate within expanded digital ecosystems that include hundreds or even thousands of third party suppliers and partners. Threat actors are exploiting these connections to circumvent traditional security measures and reach their targets.
Here, we’re focusing on how supply chain tactics can be used to exploit Salesforce platform through integration with third party systems. As a critical part of thousands of organizations’ customer relationship infrastructures, Salesforce cloud is a one of attractive targets for threat actors seeking access to sensitive data.
Gartner predicts that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains.
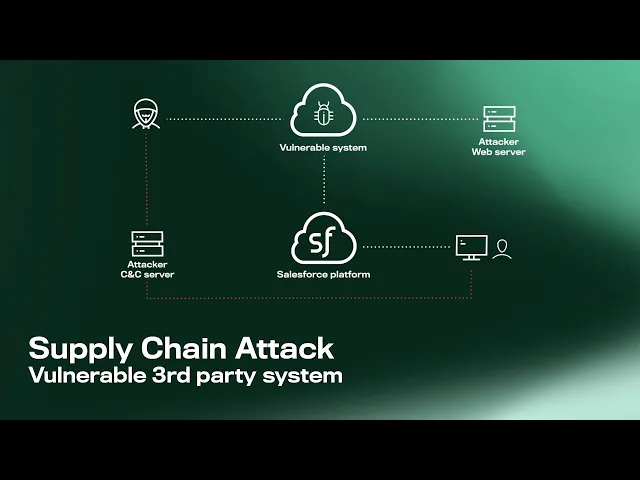
A plausible supply chain attack may begin with the threat actor discovering a vulnerable system connected or integrated with Salesforce platform. The vulnerable system can be any software or application sending or receiving structured or unstructed data to/from Salesforce platform via REST, SOAP or other APIs. The attacker can exploit a known or unknown vulnerability (such as notorious Log4j bug) within the application to compromise it and gain access to its capabilities.
If the vulnerable application has privileged access to the Salesforce platform, the attacker will be able to change permissions, modify sharing rules or tamper data in order to disguise lateral movement and abuse Salesforce’s own connections to further their attack.
Even without priveled access, the attacker may seek to exploit Salesforce platform by attaching malicious files or sending phishing links to Chatter, Case, Account, Lead or other standard or custom objects usually present in Sales, Service or Exprerience Cloud environments.
Salesforce users then download a malicious file or open a phising link from their endpoint device. The end point device may be unprotected, misconfigured or have a vulnerability, which would enable the attacker to run malicious payload or steal user credentials. Depending on how the Salesforce system is used by the organization, this could hit employees, partners, and customers.
From here the adversary can launch their real attack, likely establishing command and control (C&C) functionality in the user’s device to take over their machine and utilise its access permissions. Now the attacker can begin exfiltrating critical data or planting more malware in the network of the organization, or even expanding to other third parties.
Watch this short dynamic video to see the anatomy of such an attack in action.
*Gartner Press Release, “Top Trends in Cybersecurity 2022”, Published 18 February 2022 By Analysts: Peter Firstbrook, Sam Olyaei, Pete Shoard, Katell Thielemann, Mary Ruddy, Felix Gaehtgens, Richard Addiscott, William Candrick. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
BOOK A DEMO
Secure your Salesforce today
Tailored for high compliance sectors, our certified solution safeguards Salesforce clouds for global enterprises, including finance, healthcare, and the public sector.
Fill the form and get:
Free 15-day trial
Personalized Salesforce security risk assessment report
Demo and a solution consultation
Support from our experts with setup and configurations
