Parking scams using fraudulent QR codes have been wreaking havoc in popular tourist cities across Europe and North America recently. Have you ever considered that malicious QR codes could infiltrate your Salesforce? Our threat intelligence team has observed these well-masked threats frequently in Salesforce environments in 2025. Read on to learn what QR code attacks look like, why Salesforce is an attractive target for them, and how you can stop them.
The rise of quishing
It’s not long since Police Service of Northern Ireland (PSNI) Cyber Crime Centre, posted a notice about malicious QR codes in phishing attacks. Quishing, or QR code phishing, involves the deceptive use of QR codes to lure unsuspecting individuals into visiting malicious websites. There they are tricked to reveal personal credentials, or unknowingly download malware. QR codes are used for everything from restaurant menus to ticket validations. At the the same time, cybercriminals have found ample opportunities for exploitation. Distinguishing between legitimate and fraudulent QR codes is difficult for human eyes. Fortunately, there are preventive security technologies against QR code quishing attacks – also for Salesforce.
Examples of quishing attacks in the wild
A typical quishing email might mimic an official communication from a known corporation. It can for example urge the recipient to scan a QR code to handle something urgent, like reset a password or verify an account.
Another method involves embedding a QR code inside a seemingly innocent message related to work processes like payroll or security updates. One of the recent examples targeted a major energy company in the US with a campaign that imitated a Microsoft security notification.
On the other hand, scammers have also found ways to abuse QR codes scams in public spaces. Such example is the recent QR parking scam in popular tourist cities across UK. The scam involves malicious QR codes, often placed on parking meters, that direct users to phishing websites. Unsuspecting victims enter personal information, including payment details, under the guise of paying for parking. As a result, they potentially face double trouble with both financial fraud and a parking ticket.
10,000 victims have already fallen for the said parking scam in a matter of two months. Therat actors have launched similar campaigns across Europe, United states and Canada. These scams often target tourists who are not familiar with the local parking apps, thus easier to deceive.
The quishing attack kill-chain
In the digital world, quishing typically begins with a QR code sent via email or text. The recipient then scans the code with a mobile device. The victim is then redirected to a harmful site.
The phishing site typically mimics a legitimate business resource, login page, or document portal. The page then prompts the employee to enter their credentials or download a file.
By entering their credentials, employees inadvertently provide attackers with access to their corporate accounts. Attackers can use the credentials to harvest sensitive information or launch an attack within the organization.
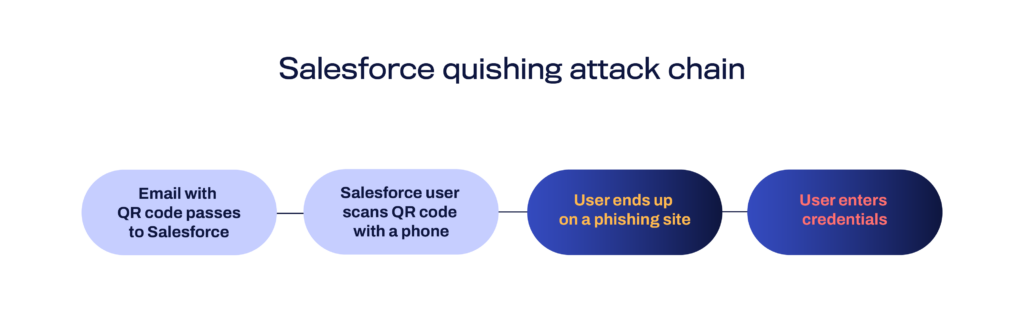
The process capitalizes on the established trust in QR codes. QR codes are handy to roll out covert operations. Quishing attacks are often harder to detect than traditional phishing attacks, or ones with the malicious link plainly imbedded in the message text. As these codes simply appear as nondescript, benign images, they bypass usual text-based URL scans implemented by most email and collaboration security systems.
QR code phishing tactics:
- Integration in familiar platforms: Quishing often uses popular platforms to reach a broad audience, and to exploit trusted services and brand names to increase the success rate of attacks.
- Sophistication in execution: By embedding malicous QR codes within messages, attackers can bypass conventional security measures which might not scan URLs embedded in images.
- The psychological play: The decision to scan a QR code often happens impulsively, thanks to the established norm of their use in safe contexts. This impulsivity is what quishers count on, reducing the victim’s likelihood of pausing to consider the potential dangers.
What makes QR code phishing especially tricky on Salesforce
All in all, malicious QR codes pose a significant threat to enterprises, and when delivered through platforms like Salesforce, they can be particularly effective and damaging. WithSecure’s Threat Intelligence Unit has discovered that malicious QR codes delivered through Salesforce have been rising in attacker popularity in 2025. Here’s why Salesforce is a lucrative vector for such attacks, and why you should secure your platform without delay:
High trust environment
Users view Salesforce as a trusted platform for daily tasks in sales management, and customer support. Employees are less vigilant about scrutinizing communications received through this platform, assuming a baseline level of security and trust. This trust can make QR codes sent through Salesforce particularly effective as employees may be quicker to scan them without suspicion. The scam itself could even leverage Salesforce’s brand identity. QR codes also employ common and seemingly harmless image types, decreasing suspicions.
Widespread use in organizations
Especially large enterprises use Salefsorce widely, which provides a broad attack surface. Malicious QR codes distributed through Salesforce can potentially reach a large number of users quickly, making it the attackers dream.
Mobile device engagement
Salesforce is frequently accessed via mobile devices, which aligns well with the nature of QR code scanning. Mobile devices are often less secure than desktops, with users typically having weaker security controls and being more prone to overlook security prompts when they are on the move. If bring-your-own-device (BYOD) is allowed, the mobile device may be a personal unmanaged device, with even weaker security measures in place.
No antiphishing blocking the way
While Salesforce offers robust security features, there are no antiphishing capabilities by default – nor antiquishing. Attackers know that there likely is no layer of protection in the Salesforce environment to detect or prevent the distribution of malicious QR codes, opening a pathway for the attackers.
You need more than awareness to prevent Salesforce QR code quishing
While educating users about the potential threats of randomly scanning QR codes is without a doubt important, true prevention requires a multifaceted approach:
- Advanced threat protection: You should implement antiphishing security solutions that can recognize and examine QR codes within Salesforce uploads, analyzing the linked URLs for malicious content before they reach end users.
- Regular security audits: Incorporating QR code-based phishing into routine security audits and risk assessments helps identify and remediate security gaps. Make sure to ensure that Salesforce is covered thoroughly in security audits.
- Limit access privileges: Although Salesforce has enforced multi-factor authentication for MFA for internal users, it’s wise to limit access rights to what a user’s role requires, and follow the least privilege approach.
- Update software and configurations: Ensure all integrations are updated with the latest security patches, and verify that your antiphishing scanning solution is properly configured to detect malicious QR codes.
- Limit use of BYOD: Some of the biggest vulnerabilities lie when employees use personal devices outside corporate security measures to access phishing sites that harvest account credentials.
- Educate Salesforce users: Continuously educate users about the risks associated with QR codes, emphasizing the need for vigilance even when using trusted platforms like Salesforce.
Block malicious QR codes on Salesforce automatically
You need a blend of vigilance and advanced security solutions to prevent covert phishing tactics – like quishing – on Salesforce. Luckily you can protect your data and Salesforce users from these hidden scams behind simple scans. WithSecure™ Cloud Protection for Salesforce scans malicious URLs in Salesforce text fields, behind QR codes and within uploaded documents. Our AntiQuishing feature was built as a response to a real-life phishing attack that our enterprise customer faced, where their Salesforce environment was the target of malicious QR codes.
Contact our team for a free consultation, take our free Salesforce risk assessment (done in minutes, no access to your environment needed), or test drive on AppExchange right away.
Salesforce AntiQuishing
Protect your Salesforce environment against advanced ransomware and phishing attacks in real-time. Natively integrated WithSecure™ Cloud Protection for Salesforce is up and running in minutes.


