Real-life evidence of NRD risks
Cyber attackers use phishing in the majority of data breaches – IBM reports a staggering 41% of all attacks attributed to it, while Deloitte notes that phishing accounts for two in every five attacks. The Anti-Phishing Working Group (APWG) underscores that 77% of phishing domains are specifically registered for malicious purposes. These domains frequently serve as launchpads for extensive phishing and malware attacks, making their scrutiny a critical security practice.
Similarly, Interisle Consulting Group observed that a significant increase in phishing is linked to the use of domain names, with an 85% jump in domains used for cyberattacks.
Research from Palo Alto reinforces these concerns, and indicates that at one point, over 70% of newly registered domains (NRDs) were “malicious,” “suspicious,” or “not safe for work.” This statistic underscores the consistent risk posed by newly established domains over the years.
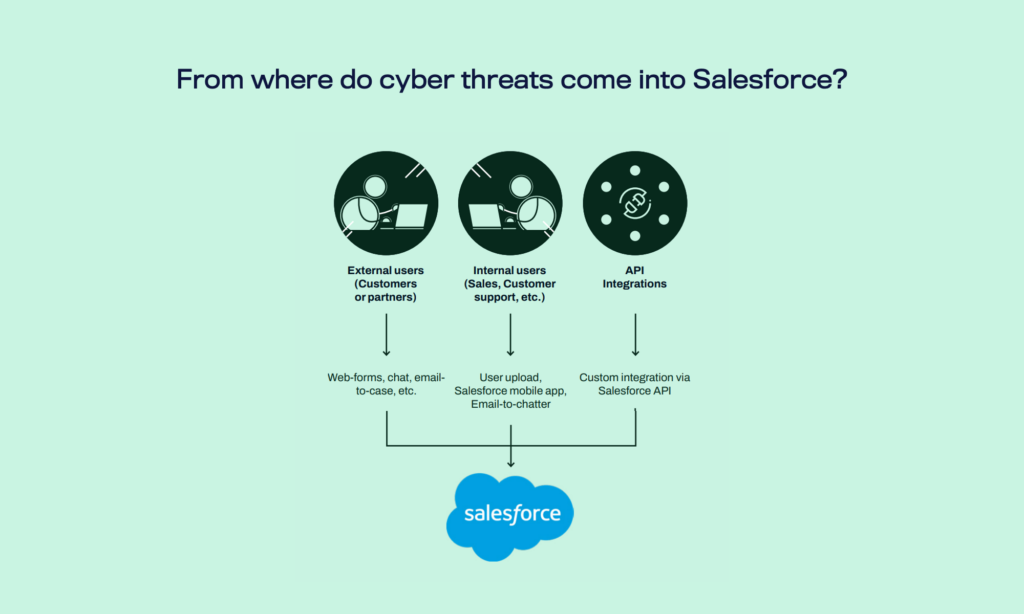
NRDs are employed not only for phishing but also as vectors for malware distribution and command-and-control operations. Cybercriminals can rapidly register and activate new domains. In response, they can rapidly deploy and evolve their attacks, and bypass traditional detection methods. This creates urgent challenges for cybersecurity defenses in environments like Salesforce.
Why combating phishing on Salesforce is crucial
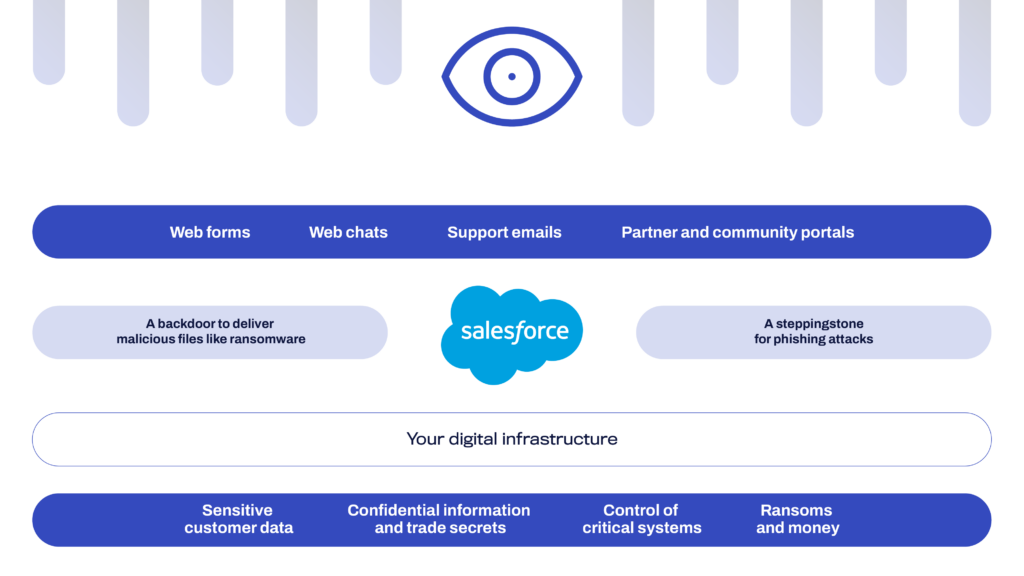
Phishing attacks pose a significant threat to organizations using Salesforce, exploiting the platform’s extensive functionalities to carry out sophisticated cyberattacks. These threats primarily target human error, using deceptive emails or malicious URLs to manipulate users into divulging confidential information such as login credentials, thereby compromising entire systems.
- Data integrity and security: Salesforce serves as a repository for vast amounts of sensitive corporate and customer data. Phishing attacks gain unauthorized access to data, causing data breaches that severely damage a company’s reputation and lead to substantial financial losses.
- User trust and compliance: Customers trust organizations to safeguard their personal information. A successful phishing attack can erode this trust, damage customer relationships, and potentially violate compliance regulations that protect user data.
- Operational continuity: Phishing attacks disrupt the normal business operations of Salesforce, which leads to downtime and decreased productivity.
Proactive NRD blocking is the simplest and the most effective strategy
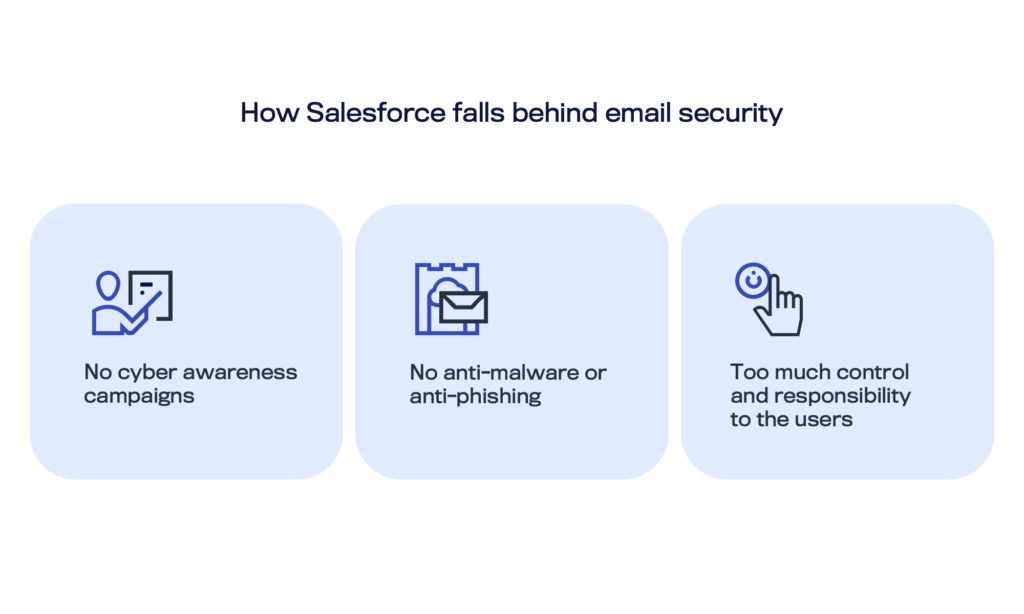
Managing NRD threats effectively requires a combination of technology and strategy tailored to an organization’s specific risk tolerance. Although user awareness is important, no Salesforce user should be expected to act as a phishing detective. Enterprises with low risk tolerance should proactively block NRDs from interacting with their Salesforce systems.. By utilizing real-time intelligence, WithSecure Cloud Protection for Salesforce empowers organizations to selectively block NRDs. The solution analyzes the domain’s age. Customers can configure settings to block domains registered within recent time frames, including 7, 14, 30, 60, or 90 days.
Incident response insights
Our incident response team has identified attacks on Salesforce environments where NRDs were a factor. These observations have reinforced the need for robust NRD management and influenced the development of product features that meet the stringent compliance requirements of many enterprise customers. These customers often mandate that newly created domains should not gain access to their Salesforce platforms.
“Many enterprises, particularly financial institutions, have stringent requirements. For instance, they mandate that domains less than 32 days old are not allowed on their network or platform ,” Anssi Korpilaakso, Director of Business Operations at WithSecure Cloud Protection for Salesforce, concludes.
The problem calls for systemic intervention
To curb the misuse of newly registered domains (NRDs) in cyberattacks more effectively, authorities need to take broader regulatory actions instead of merely placing the responsibility for risk management on the victims.
- Regulatory oversight: Authorities could impose stricter controls on service providers that disproportionately enable cybercriminals, possibly penalizing those that consistently supply the means for cyberattacks.
- Identity verification: Introducing stringent identity verification or certification requirements for bulk domain registration can prevent misuse by making it harder for cybercriminals to anonymously acquire domains.
- Limiting resources: Restricting the number of accounts and subdomains one can register with free or inexpensive web hosting services could curtail the ability of attackers to proliferate harmful domains.
- Automated monitoring: Deploying automated systems to monitor and screen suspicious registration and usage patterns can preemptively catch potentially malicious activities.
Comprehensive phishing protection – 100% Salesforce-native
WithSecure™ Cloud Protection for Salesforce enhances defenses against URL-based threats, including the risks associated with newly registered domains (NRDs). This constantly updated suite of URL scanning features actively addresses the hidden dangers of malicious URLs within Salesforce.
Stop phishing and url-based threats instantly: URL Protection feature actively guards against phishing and malicious websites. It scans URLs upon upload and when clicked. This real-time scrutiny is crucial for intercepting threats before they impact your system.
Dynamic protection against evolving threats: The nature of URL threats is volatile. A link that was once deemed safe can turn malicious later. Click-Time URL Protection feature dynamically evaluates URLs at the point of access and adapts to the mutating threats.
Block newly registered domains: You can block access to domains based on their registration age. Settings are adjustable from 7 to 90 days old domains. This effectively reduces the risk of falling victim to attacks that are launched from newly established malicious sites.
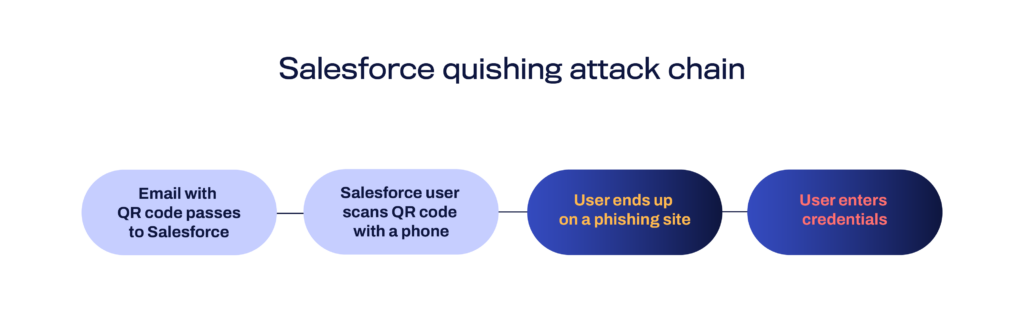
Comprehensive detection of malicious URLs: The solutions detects and blocks harmful URLs that are within files and behind QR codes. This extends protection beyond visible links in text fields. This comprehensive approach helps thwart hidden malware and phishing attempts encoded within document uploads.
Block shortened URL threats: Shortened URLs, often used for their convenience, can mask dangerous destinations. Our system ensures every link is verified, enhancing security against camouflaged threats that could otherwise bypass detection.
Tailored security for high compliance sectors: We have designed the solution with the needs of highly regulated industries in mind. Robust protection aligns with the stringent security requirements of finance and public sectors.
Concerned about malicious URLs entering your Salesforce environment? Contact our team for a free consultation.