Salesforce attacks are increasing, as the platform has become a prime target for cybercriminals. Salesforce is an attractive target due to its high level of connectivity and the volume of sensitive personal and commercial information it contains.
Salesforce environments now sit directly in the path of cyberattacks.
“The targeting of organizations’ SaaS services that hold and process sensitive data has become an extremely popular TTP of ransomware actors. It has become apparent that actors no longer need to spend a lot of time and money seeking to fully compromise a network, when extortion demands based on sensitive data theft can be just as successful. It enables an effective and scalable way of targeting organisations at scale,” explains Tim West, Director of Threat Intelligence at WithSecure. “The business value of Salesforce and the level of sensitive data held within Salesforce makes it an exceptionally attractive target for financially motivated Threat Actors.”
Salesforce attacks have resulted in data breaches
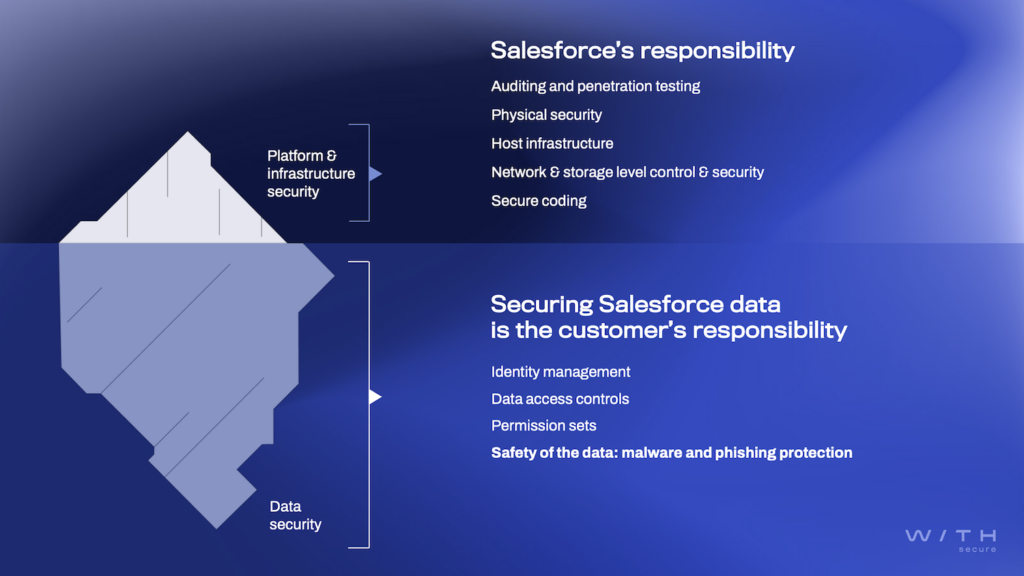
Threat actors adapt fast. They aren’t focusing on technical exploits. They’re exploiting access, trust, and human behavior. Salesforce is a perfect environment for this. Salesforce doesn’t have a built-in antivirus. It doesn’t scan incoming data for cyber threats. Securing the data and users of the platform is the customer’s responsibility. Attackers are aware of this gap.
The UNC6040 campaign: from vishing to connected apps
In 2025, Google’s Threat Intelligence Group reported on a campaign by UNC6040 – a financially motivated group targeting Salesforce with a blend of social engineering and OAuth abuse.
Credential harvesting was the first step. Attackers gained access through reused or phished credentials tied to single sign-on (SSO) systems. Once authenticated, they moved laterally within environments using the victim’s privileges, often unnoticed. OAuth abuse worsened the situation, allowing attackers to generate long-lived access tokens that bypassed MFA and evaded traditional security alerts.
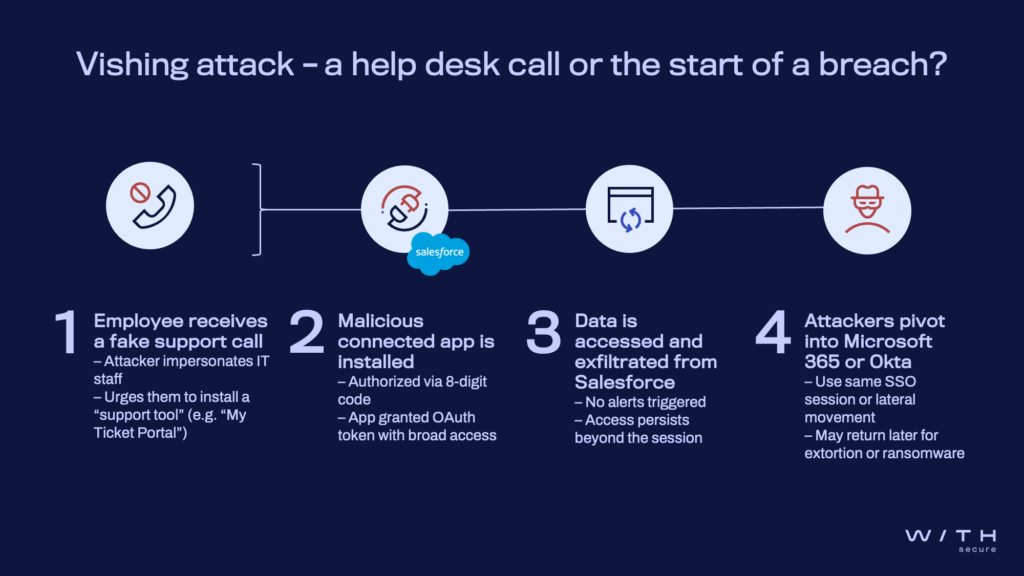
These Salesforce attacks didn’t rely on technical exploits. Just an 8-digit authorization code – which is the default for installing a connected app in Salesforce – was enough. Once installed, malicious apps weren’t inspected by native tools, leaving the door wide open.
Attackers impersonated IT support. Using voice-based social engineering tactics, like voice phishing (vishing), they persuaded employees to install a fake version of the Salesforce Data Loader – often called “My Ticket Portal” – through the Connected Apps interface. This provided persistent access, enabling attackers to extract data directly from Salesforce, pivot into Microsoft 365 and Okta, and return weeks later with extortion demands.
The methods used by UNC6040 are nearly identical to those of UNC3944, better known as Scattered Spider.
“Attribution is hard, particularly to Scattered Spider,” West notes. “They’re often described as a loosely organized ‘collective,’ revolving around forums and social channels known as ‘The Com’. Groups like UNC6040 – sometimes observed directly targeting Salesforce through modified apps – share overlapping behaviors with UNC3944. It’s even possible there’s a direct connection.”
While these two groups are technically tracked separately, their tactics, infrastructure, and behavioral patterns suggest they could be the same actors or closely affiliated.
UNC3944 (Scattered Spider): silent exfiltration at scale
UNC3944, or Scattered Spider, is known for precision-targeted attacks that exploit trust and identity. Like UNC6040, they frequently begin with compromised credentials – often phished or purchased – and escalate access via manipulated IT support processes.
Once inside, they authorize third-party tools such as Airbyte and Fivetran to silently exfiltrate cloud data. Their techniques include:
- Persuading help desks to escalate permissions
- Exploiting identity provider (IdP) integrations
- Establishing virtual machines for persistence and staging
“Scattered Spider deploy social engineering to gain access to SaaS environments. Their attacks may look technically simple, but that doesn’t make them any less dangerous,” West adds. “They’ve been linked to the MGM and M&S breaches, and even tenuously connected to the Snowflake mass compromise. If your organisation runs Salesforce in the cloud, it’s highly likely actors like these are already looking at you.”
Their goal isn’t disruption – it’s long-term data theft, often invisible until it’s too late.
From help desk to breach: The same tactics behind the UK’s retail cyberattacks
In May 2025, major UK retailers including M&S, Co-op, and Harrods were forced offline by a wave of ransomware and data theft attacks. Investigators believe the same group, Scattered Spider (UNC3944), is behind these incidents.
What happens next is where the real damage begins: lateral movement, data exfiltration, and extortion. All from inside a trusted, integrated system.
Airline sector attacks: Scattered Spider shifts focus
In June and July 2025, multiple aviation companies – including Hawaiian Airlines, and WestJet – were targeted in a coordinated wave of cyberattacks attributed to Scattered Spider (UNC3944).
This shift fits Scattered Spider’s known pattern: targeting one sector at a time in focused campaigns. After retail and insurance, aviation has become the new focus, which makes further attacks on the sector likely.
Following the breach, the FBI publicly warned that the aviation industry is now an active focus for Scattered Spider. The group’s methods remain consistent: impersonating IT support staff, manipulating help desks (both internal and outsourced), and bypassing MFA to gain trusted access. Contact centers are a known soft spot. They’re often targeted first due to their broad access and lower security controls.
Security researchers from Mandiant and Palo Alto Networks have confirmed this campaign aligns with Scattered Spider’s known playbook, particularly its use of social engineering and support workflow abuse.
In some cases, attackers reportedly used deepfake audio to impersonate employees and persuade help desk staff to authorize rogue access. Once inside, they quietly extracted sensitive data for extortion and, in some cases, deployed ransomware.
While Salesforce was not directly involved in these breaches, the tactics are strikingly familiar. Help desk impersonation, exploiting support workflows, credential harvesting, and MFA bypass are the same entry points we’ve seen used to compromise CRM environments. When trust is exploited in one system, access to others is often just a few steps away.
“Organizations need to be conscious that when outsourcing administrative functions – such as help-desk or management of Salesforce services – they are also extending their threat surface, and outsourcing security culture. There is no ‘silver-bullet’ technology that mitigates human risk,” West highlights.
Coca-Cola: Middle East employee data leak
In May 2025, the Everest ransomware group attacked Coca-Cola’s operations in the Middle East. The group accessed and leaked over 1,100 HR files, including:
- Personal identification documents
- Salary and banking details
- Internal org charts and account structures
The breach affected nearly 1,000 employees across the UAE, Oman, and Bahrain. Reports indicate that Salesforce file access was part of the attack chain.
Coca-Cola Europacific Partners: 23 million records exposed via Salesforce
In a separate incident, the Gehenna group breached Coca-Cola Europacific Partners (CCEP) Salesforce dashboards and exfiltrated over 23 million records. This included:
- 7.5 million account records
- 9.5 million customer service cases
- 6 million contact entries
- 400,000 product records
Sample data was published on public breach forums. The attackers also contacted employees, signaling intent to sell or release more data unless paid.
Why this matters, and what comes next
Salesforce is central to how many organizations operate. It holds loads of sensitive customer records, sales data, intellectual property, and internal support content. Files and links flow through it every day. It’s deeply integrated with other cloud services.
This level of access and automation makes it highly attractive to attackers. And yet, Salesforce environments often operate without the same level of monitoring or control applied to other enterprise systems.
When observing Salesforce attacks, we’ve seen phishing links embedded in business documents. Data exfiltrated directly from support systems. Malicious files distributed via workflow automation. Each case shows how attackers use Salesforce’s built-in functionality to move laterally or extract high-value data.
This isn’t hypothetical. Threat actors are already targeting Salesforce directly – using impersonation, stolen credentials, and OAuth abuse to establish long-term access. The UK retail breaches show just how public and damaging these tactics have become.
If that’s already happening, the next question is clear: what happens when even more threat actors start treating Salesforce as the new and effective entry point?
Identity-based attacks are the common thread
Many of these Salesforce attacks don’t rely on technical exploits but succeed through access. And that access often begins with compromised credentials.
The compromise might come from a phishing link. Or from login details exposed in a third-party breach. Credentials dumped on the dark web are frequently reused across systems, giving attackers an easy way in.
This isn’t just a backend hygiene issue anymore — it’s a front-line security gap. As attackers increasingly exploit legitimate access methods and IT support workflows, even one reused password or stolen credential can open the door to Salesforce… and everything it connects to.
An evolving risk surface
Threat actors are shifting focus to systems where trust is built in. They don’t need to break through technical barriers when users are already opening the door, whether by approving a connected app, using single sign-on without MFA enforcement, or responding to a convincing IT support call.
The Salesforce threat surface is expanding:
- Users are uploading and sharing more files
- Portals and agents interact with customers at scale
- Connected apps have broad privileges, often without visibility
- Credentials are being reused or phished, giving attackers direct entry into CRM environments
In many cases, once a credential is compromised, attackers can quietly authenticate, pivot across cloud services, and extract data without triggering alarms. Access can be maintained long after the initial compromise.
Without inspection and control, these access pathways become vulnerabilities. And the cost of exposure – operational, legal, reputational, strategic – can be difficult to contain.
What you can do next in light of Salesforce attacks
You can’t prevent every phishing email. You can’t control which credentials show up on the dark web. And no help desk workflow is completely immune to social engineering.
But you can still take control over what happens next. And as these recent Salesforce attacks underline, proactive security strategies are key.
These practical recommendations help reduce risk across identity, access, and content:
Audit and visibility
Audit connected apps and user activity in Salesforce. Regularly review and revoke unused or high-privilege accesses. Monitor for suspicious login behavior.
Identity and access controls
Enforce MFA across all user roles and integrations. Apply least privilege principles and limit admin access. Harden IT support processes against impersonation tactics. Include Salesforce in access governance reviews.
Credential compromise monitoring
Ensure you can detect credential compromise, rapidly revoke access, and restore clean Salesforce configurations and data when needed.
Real-time content protection
Use natively integrated threat protection to inspect files and links directly in Salesforce. Minimize human error by preventing phishing links and malware from spreading through cases, chats, and portals – not just email.
Phishing and user awareness
Educate users about social engineering methods, voice phishing, and fake app installs targeting Salesforce. Include Salesforce-specific tactics in security awareness programs.
Third-party systems and integration risk
Review and vet all connected apps and external platforms, especially support tools, help desks, and ticketing systems. Apply phishing-resistant MFA and strict identity verification to any system integrated with Salesforce.
Incident response preparation
Include Salesforce in incident response and recovery plans.
Real-time protection against cyber attacks targeting Salesforce
WithSecure Cloud Protection for Salesforce delivers the security visibility and control that traditional tools miss, directly inside Salesforce.
It stops malicious files and phishing links before they reach users.
It inspects content shared via email, portals, cases, and automation in real time.
And soon it monitors compromised credentials used to access your Salesforce environment.
While attackers are adapting fast, your defenses can too.
WithSecure Cloud Protection for Salesforce closes the Salesforce security gap across your workflows, and is set-up with a only few clicks.
By mitigating threats such as credential compromises, credential phishing and malware delivery, our Salesforce native security layer stops the breach before it spreads.
Prevention is always cheaper than recovery.