New attack surface, new urgency
Agentforce security – the new security aspect to consider in 2025.
Agentforce is changing how you work — and how attackers get in.
AI agents now handle sales, service, and support autonomously, rapidly processing vast amounts of data. But while your operations scale at agentic speed, your attack surface does too.
There’s no built-in scanning for files or links. No phishing awareness in agents. No default safety net.
Malicious content moves at machine speed. That means threats like malware or credential phishing can flow through Agentforce workflows instantly: uploaded by a user, retrieved by an agent, delivered to your team or customers.
And attackers have noticed. Recent campaigns by groups like UNC3944 show how SaaS platforms like Salesforce are now primary targets for phishing, identity compromise, and lateral movement. As attackers shift toward SaaS platforms like Salesforce, this new AI-driven workflow introduces real risk.
Unless your security keeps pace, Agentforce could automate risk as fast as it automates work.
Securing Agentforce data is your responsibility
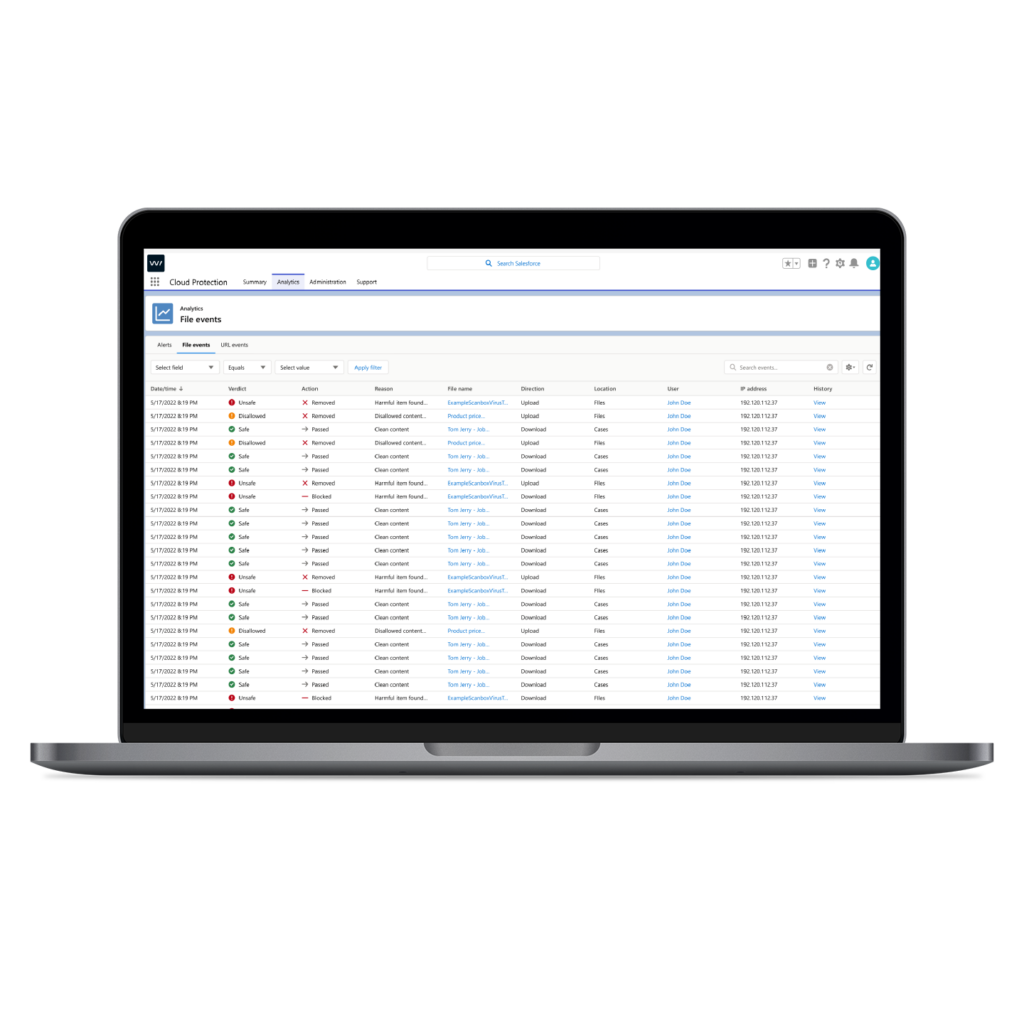
Agentforce accelerates business. But it also accelerates risk. AI agents process files and URLs from portals, forms, and integrations like Slack or WhatsApp, without human review or built-in threat scanning.
That means your security perimeter now includes:
- Phishing links: Instantly shared by agents, leading to credential theft or account compromise.
- Malicious files: Uploaded by customers or partners, containing ransomware or other threats.
- Human-agent interactions: Agents hand off data to employees, spreading threats across teams.
- Collaboration tools: Shared files and links extend risk beyond Salesforce to every connected tool.
Salesforce doesn’t scan this content by default. And agents don’t know how to spot threats.
According to the Shared Responsibility Model, it’s up to you, the cloud customer, to secure the data flowing in and out of your Salesforce environment. Whether it’s touched by a human or an agent, protecting that data is your responsibility – including how it’s configured, accessed, and what’s allowed to pass through.
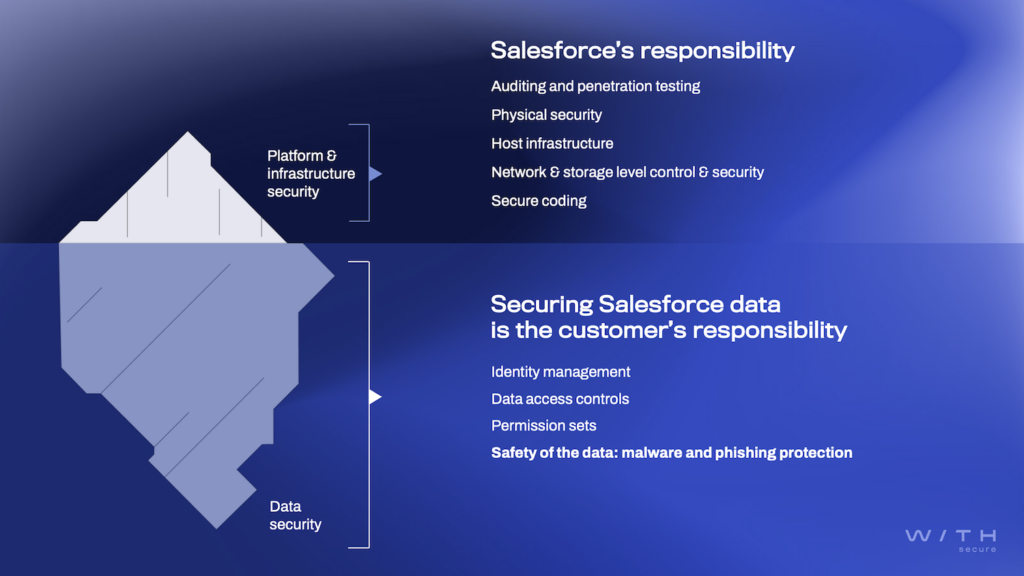
What an Agentforce attack path looks like
Without real-time scanning, threats can move faster than your defenses.
Imagine this:
- A customer uploads a file through your portal, which it looks like a PDF, but it’s hiding malware.
- An AI agent retrieves the file to process a support request or sales inquiry.
- The agent sends it to an employee or forwards it to another tool like Slack or email.
- The file is opened and malware executes. It’s already inside your environment.
- From there, it spreads laterally, compromising accounts, data, and connected systems.
No human saw the file. No one clicked a phishing link. But the threat still made it in.
This is how agentic speed becomes attacker speed. Unless you scan every file, URL, and agent action in real-time.

How to secure Agentforce workflows
Agentforce makes decisions in seconds. Your security needs to move even faster.
WithSecure™ Cloud Protection for Salesforce is built to protect both human and agent workflows in real time. It operates right inside the Salesforce platform. No delays, no friction, no missed threats.
- Real-time protection at agent speed
Files and URLs are scanned instantly at upload, download, click, or agent retrieval before they can cause harm. Our detection completes faster than most AI agents can act. - 100% Salesforce-native integration
No external processing. No added complexity. No hidden vulnerabilities. Just seamless, frictionless, certified protection inside the platform. - Secures every interaction
From customer uploads and portal forms to collaboration tools like Slack or WhatsApp — threats are intercepted wherever they enter. - Built for uptime and trust
Protects workflows without disrupting AI autonomy, ensuring agent efficiency and security go hand in hand.
Preparing for scale
Agentforce adoption is only accelerating. As your teams deploy AI across more workflows and process more unstructured data, the security stakes grow just as fast.
More files. More links. More risk – unless your protection can keep pace.
WithSecure™ Cloud Protection for Salesforce helps you stay ahead of these changes. Our native solution scales with your AI transformation, giving you:
- Consistent protection across all agent and human touchpoints
- Real-time coverage that scales as fast as your workflows do
- Confidence to expand, knowing your security keeps up with your AI transformation
Agentforce will help you move faster. We make sure you move securely.
Still have questions?
At WithSecure™, we’re committed to helping you make the most of Salesforce and Agentforce while fulfilling your security responsibilities. Together, we can ensure your agent-powered digital transformation is secure, seamless, and future-ready. If you’d like to learn more about how we can help safeguard your workflows, let’s connect.
Doesn’t Salesforce protect against these threats already?
Salesforce doesn’t scan links or files shared in Agentforce workflows unless you implement an additional security layer. It’s your responsibility to protect the data flowing through your AI workflows and automations.
We already have endpoint/email protection. Isn’t that enough?
Files and links can bypass traditional tools completely. If your AI agent clicks a phishing link or opens a malicious file inside Salesforce, your other tools may never see it. Only a native solution scans content where the agent acts, and at the point of entry.
How does this integrate with our setup?
WithSecure™ Cloud Protection is 100% Salesforce-native. It integrates seamlessly with your environment – no external routing, no added complexity, and no impact on agentic performance. The Agentforce extension comes with the main managed package at no additional cost. There’s no separate management portals or interfaces, no extra charge.
What makes this better than other security tools?
Only WithSecure scans inside Salesforce in real time — at the point of agent action. Competitors scan externally, after the fact, or not at all. That’s why real-time + native + agent-aware protection is unmatched.
Is this compliant and auditable?
Yes. You get full audit-ready logs, policy history, and certified trust (ISAE 3000 Type 2 / SOC 2 Type 2, ISO 27001). Every scan and decision is traceable, even the seemingly invisible agent actions.
Secure your agent workflows — in real time, with zero friction
WithSecure™ Cloud Protection protects what Agentforce accelerates. Real-time file and link scanning. 100% native. No added cost. No added complexity.