The state of play for digital supply chain risk
The digital supply chain offers unparalleled flexibility and freedom, enabling organizations to rapidly acquire new capabilities and seize opportunities. But it also comes at the cost of increased cyber risk exposure.
Introducing a web of thousands of moving parts makes it extremely challenging to maintain effective visibility of the IT estate and identify potential vulnerabilities.
However, threat actors are also actively seeking to exploit these connections. Attacking third party connections such as SaaS suppliers or software plugin developers enables cyber criminals to bypass security defenses and potentially strike at the heart of an organization’s network. This connectivity can be exploited to deploy malware, including highly destructive targeted ransomware, within the target business, exfiltrate high-value data, or establish command-and-control.
Gartner® has named digital supply chain risk as one of the leading security and risk management trends for 2022 and predicts that, “by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.”1
Indeed, it has already been estimated that supply chain attacks have tripled in 2021 alone. Some of the biggest data breaches of the last year have centered on digital supply chains.
Log4Shell
This high-profile exploit affected the popular Apache Log4j 2 java library used for logging error messages. The vulnerability, officially CVE-2021-44228, enabled an attacker to gain remote access to a device running certain versions of Log4j 2 through text messages. The flaw was discovered and quickly patched in December 2021 but may have been around since as early as 2013. It is thought that nearly half of all organizations may have bene targeted using the vulnerability at some point.
Okta
In March 2022, secure MFA provider Okta announced that it had suffered a major security breach in January that impacted hundreds of customers. The breach demonstrated how third-party connections are targeted and exploited, as it began with the compromise of a sub processor supplying Okta. The attackers, a hacking group known as Lapsus$, was then able to enter customer networks and access data using a remote desktop tool.
Office 365
Threat actors have increasingly targeted the extended Office 365 environment in targeted phishing attacks. The victims are first hit with an email prompting them to login into their 365 account and verify a new application. Rather than the usual imitation phishing site, the email links through to the user’s genuine Office 365 login page. The threat is the application itself, which will provide the attacker with access to the user’s files and emails. Because it is already within the environment, the rogue application can circumvent the need for multifactor authentication (MFA).
SolarWinds
Despite occurring in 2020, the SolarWinds attack remains the most notorious example of a high-end digital supply chain attack. Widely believed to be the work of Russian-backed operatives, the incident saw software vendor SolarWinds breached in a sophisticated multi-pronged attack that targeted its popular Orion solution. The perpetrators covertly injected malicious code into an update for the software, enabling them to access the networks of thousands of users, including governmental bodies such as the US Treasury and Justice department.
How third-party integrations introduce new threats to Salesforce
Salesforce is an essential asset for many organizations, often playing a defining role in their entire customer management and digital experience strategy. As such, there is a huge market demand for the ability to customize and configure the environment to suit different operational needs
The Salesforce platform can be heavily customized and extended with third party applications, components and cloud services. Salesforce AppExchange, the platform’s official app store, offers more than 3,400 apps, and organizations can also connect their Salesforce environments with external systems or applications via SOAP or REST APIs. Those systems may be hosted in different cloud environments and use a variety of proprietary or open-source software. In addition, Salesforce platform supports traditional email or web-form based integration
With so many options, enterprises are guaranteed to find third-party support for any adaptions and extensions they want to apply to their Salesforce environment. However, each new addition also increases the organization’s exposure to digital supply chain risk.
There are multiple potential threats here:
- Malicious imposters
- Compromised software
- Vulnerable code
The threat within
Like any other digital environment, Salesforce can become highly vulnerable when it has not been correctly configured.
Misconfigured applications and ineffective identity management can quickly leave the environment exposed. Threat actors are adept at sniffing out poorly secured user accounts and applications that have been left with their default settings in place. Weak access controls make it far easier for cyber attackers to infiltrate the environment.
This is a serious issue even before the introduction of hundreds of new elements through third party applications and components. It can be particularly problematic for larger organizations, where a lack of coordination across branches and departments means the environment is bloated by redundant apps and plugins for the same tasks. Smaller firms meanwhile may be more streamlined but will be more likely to add new components on the fly without effective safeguards.
It should be noted that Salesforce has since taken steps to make poorly configured sharing rules more visible to help reduce the risk and has published release updates that change default settings to more secure ones. Salesforce Optimizer, a Lightning Experience application, can for example be used to conduct regular checks and highlight any potential issues around guest users.
Anatomy of a Salesforce supply chain attack
The scope and complexity of the Salesforce environent meand there are multiple ways it can be targeted and exploided as part of a digital supply chain attack. Here’s two examples of attach scenarios.
Scenario 1: Vulnerable third-party system
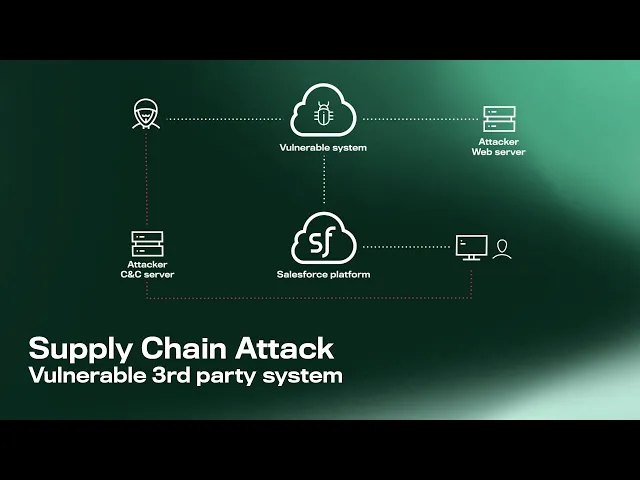
Here, the attacker identifies a vulnerability in a software application integrated with Salesforce, such as a tool that retrieves data for analysis, and exploits it to achieve remote access of the system. The vulnerable application is connected to Salesforce via API, and since these usually have a higher trust level than a human user, the attacker is able to access the system with relative ease.
The attacker may seek to steal or damage data within Salesforce but can also use the platform’s capabilities as part of their attack chain. For example, malicious documents and URLs can be seeded throughout the environment to be clicked and downloaded by unsuspecting users, including employees, customers, and other connections. These users can then be compromised, and their system access exploited to continue the attack on the rest of the company’s IT infrastructure.
Scenario 2: Compromised development tools
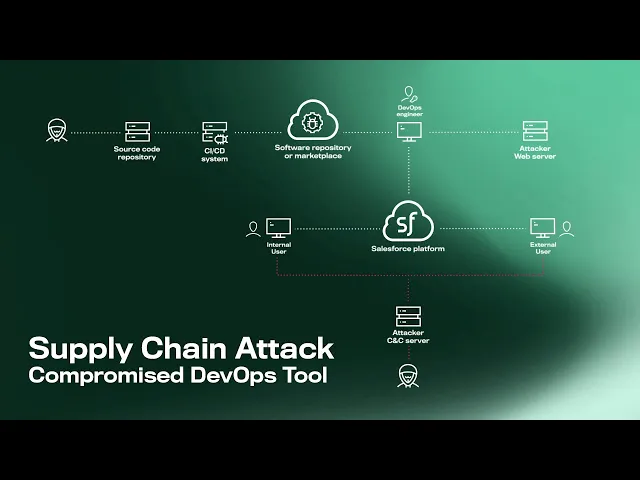
In this scenario, the threat actor first targets either a source code repository or the CI/CD system of a software vendor in order to introduce malicious code into its product. The initial system access can be achieved in multiple ways, with the use of phishing to acquire user credentials being one of the most common tactics, as demonstrated by SolarWinds.
The application or component is then integrated into the Salesforce environment, enabling the attacker to exploit its connectivity to compromise other users and endpoints. Again, from here they can achieve whatever malicious goals they have. The process may even repeat itself, with the targeted organization serving as yet another steppingstone in an extended supply chain attack.
The attacker may access the Salesforce instance directly on the first pass or may implement a backdoor and wait until the integrator has production access later on. There is a tendency for developers to blindly trust in the security of their tools, particularly if they come from a known vendor. However, as SolarWinds demonstrates, even a well-established vendor can be a source of risk if they are compromised by organized attackers.
Best practice for mitigating digital supply chain risk
Cyber security is a complex issue that cannot be solved by a single magic bullet. This is especially true for a cloud environment as large and dense as Salesforce. As such, mitigating the risk of digital supply chain attacks on Salesforce requires a multi-layered approach that combines the right security solutions with the right processes and policies. Some of the most important elements to a Salesforce security strategy include:
Implementing Application Portfolio Management (APM)
To ensure the security of the Salesforce environment, thorough vetting of all applications and components is necessary, including researching vulnerabilities and previous incidents, verifying issue resolutions, and implementing an Application Portfolio Management process. Additionally, organizations should assess the security measures of third-party vendors and consider security requirements in service level agreements, while being cautious of geopolitical factors to mitigate the risk of nation state-backed attacks.
Risk mapping potential breach impact
Organizations must thoroughly evaluate how an asset fits within their Salesforce environment and assess the potential consequences of a breach, taking into account its capabilities and connections to Salesforce and the broader IT infrastructure. Enterprises should carefully weigh the risk versus the benefits of introducing a new component and incorporate this analysis into their overall security strategy.
Gaining a centralized view of third-party assets
In complex Salesforce environments with numerous third-party components, administrators should prioritize gaining visibility to minimize blind spots and mitigate incidents. By focusing on important and high-risk elements first, implementing structured policies for introducing new assets, and gradually expanding control, they can maintain visibility and prevent the addition of redundant applications.
Eliminate misconfiguration and access issues
Besides focusing on the digital supply chain, organizations should also pay attention to their internal processes to mitigate cybersecurity risks. Conducting audits to ensure correct configuration and access management in the Salesforce environment, setting minimum access levels, disabling unnecessary sharing capabilities, and adopting a least privilege approach for user profiles and automated systems are essential measures. Regular reviews of new features and periodic in-depth assessments of system configurations are necessary, and seeking specialized expertise can help ensure comprehensive security.
Block malicious content on Salesforce
To prevent supply chain attacks and exploit through Salesforce, organizations need a comprehensive security approach that includes endpoint, network, and cloud-based protection. WithSecure offers solutions to prevent, detect, and respond to modern attacks, including their Cloud Protection for Salesforce, which scans all content in real-time to identify and block malicious files and URLs uploaded to the platform, ensuring strong protection without impacting user experience.
Implementing an effective response plan
Given the inevitability of data breaches, organizations should prepare for the possibility of a digital supply chain attack on their Salesforce environment by implementing an effective incident response and remediation plan. Utilizing services like Salesforce Shield, with features such as detailed logging and per-field encryption, can aid in incident detection and analysis. Additionally, having access to specialized skills and tools, such as those provided by a specialist partner, can help identify and remove threats within the environment, while implementing regular system backups and alternative communication methods can mitigate the impact of a compromised Salesforce environment on business operations.
Getting ahead of digital supply chain risk in 2023
Supply chain risk is growing rapidly as threat actors seek new attack paths to evade defenses
The extended Salesforce environment is vulnerable as an attack path unless organizations take precautions
Businesses should prepare now before they fall victim
Supply chain risk is an unavoidable part of doing business in the digital era. Enterprises must be aware that the threat is increasing as both their own supply chains expand, and threat actors continue to look for new opportunities to evade security defenses.
As their digital footprints expand and connect with more third parties, organizations must ensure that their ability to monitor and control the extended supply chain keeps pace.
Salesforce must factor prominently in these security plans as both a crucial CRM system, and as an environment that can be home to hundreds of different third-party elements.
While Salesforce has accountability for securing its own infrastructure, users are liable for the third-party components and content that enters the environment – an approach known as the shared responsibility model.
High-profile incidents like SolarWinds, Kaseya and Log4J have continued to dominate the headlines and raise awareness of supply chain risk. However, Salesforce is not yet part of this conversation.