Yet, there’s a silver lining. With proactive measures, your Salesforce doesn’t have to be defenseless against PDF malware. This article cuts through the digital fog, revealing how cybercriminals weaponize PDFs and showcasing how WithSecure Cloud Protection for Salesforce blocks these covert threats.
The hidden hazards of malicious files
Cybercriminals are cleverly masking malicious software, known as malware, within common file types. Malware can disrupt, damage, or gain unauthorized access to your computer systems and networks.
The various forms of malware:
- Viruses: These harmful programs latch onto files and proliferate malicious code.
- Worms: Self-replicating malware that wends its way through networks, needing no human help.
- Trojans: They trick users by pretending to be benign software while deploying malware.
- Ransomware: Holds data hostage, crippling networks until a ransom is paid.
- Spyware: Gathers personal data in secret, like your web habits and keystrokes.
- Adware: Not only annoying with ads, but also potentially a spy on user activity.
- Rootkits: They sneakily give attackers deep system access and hide their tracks.
- Keyloggers: Stealthily record keystrokes to steal passwords and other sensitive information.
Delivery mechanisms for file-based threats on Salesforce
Salesforce cloud’s digital transformation journey brings innovation and risk. The new cyber attack surfaces introduced are often outside the scope of traditional security protocols.
Malware, adept at concealment, can infiltrate systems via PDFs in email attachments or form submissions, typically from unfamiliar senders.
The peril arises when a user interacts with a dubious link or file from an unverified source, often baited by social engineering tactics.
The rise of malicious PDFs
PDFs, created by Adobe in 1992, are ubiquitous for digital documents, from manuals to contracts and invoices. This widespread trust in PDFs is precisely what hackers exploit to mask threats.
According to Palo Alto’s 2023 research, 66.6% of all email attachment malware was delivered via PDFs.
Moreover, a VirusTotal Malware Trends Report indicates a recent 500% spike in malware distribution through PDFs. New file types and evasion techniques are continually emerging, with PDFs at the forefront of these trends as reported by VirusTotal.
The formidable threat of PDFs
Built-in PDF readers in modern devices make PDFs an omnipresent threat vector. Attackers leverage the trust users place in PDFs to initiate attacks. The dynamic and interactive capabilities of PDFs, such as forms and multimedia elements, are potential malware conduits.
PDFs can execute JavaScript, a common method for distributing malware. They can also house embedded and encrypted objects that evade standard antivirus detection, posing significant security risks.
Neutralizing malicious PDFs
External PDF uploads to Salesforce through various channels need scrutiny. Since Salesforce lacks a built-in malware scanner, third-party solutions become essential. There are native apps on Salesforce AppExchange such as WithSecure Cloud Protection for Salesforce to do the job.
In the intricate web of today’s IT environments, it’s prudent to deploy a layered defense strategy, fortifying both the entry points, like Salesforce, and the endpoints, like laptops.
Selecting the right anti-virus scanner
Not all anti-virus scanners are equal. Sophisticated PDF malware requires advanced detection methods beyond signature-based scanning, such as behavioral analysis. File type spoofing, where executables masquerade as PDFs, can only be detected by more sophisticated threat protection systems.
Despite the focus on emerging threats, established malware still lurks in the digital wild, necessitating a robust signature-based detection as part of a comprehensive security strategy.
Unpacking how WithSecure Cloud Protection shields Salesforce from PDF hazards
Envision your Salesforce environment, complete with the Salesforce Service Cloud. This platform is a cornerstone of your digital customer engagement, facilitating smooth communication between clients, partners, and your team.
Central to customer support is the web-to-case form, a vital tool that permits file uploads to your Salesforce space.
Now, picture a cyber attacker orchestrating a phishing scheme through this form. They append a seemingly innocuous PDF, ostensibly part of a support query with an attached invoice. However, this file stealthily houses malware.
Upon upload to Salesforce, WithSecure Cloud Protection swiftly initiates a malware check. Employing a multi-tiered analysis fueled by real-time threat intelligence, machine learning, and heuristic techniques, the system begins its scrutiny.
The initial analysis involves comparing the file’s signature to known threats. If the file is unrecognizable, and its signature is not on record, the system escalates the inspection.
The PDF then undergoes a more nuanced behavioral analysis within the WithSecure Security Cloud. This deeper dive uncovers a concealed executable embedded within the PDF.
This hidden threat is identified as a strain of the Locky ransomware family, notorious for evading conventional antivirus measures by masking its macros within a PDF. This ransomware is engineered to hijack the user’s system, altering the desktop background to display a ransom note that provides instructions for decrypting files via payment.
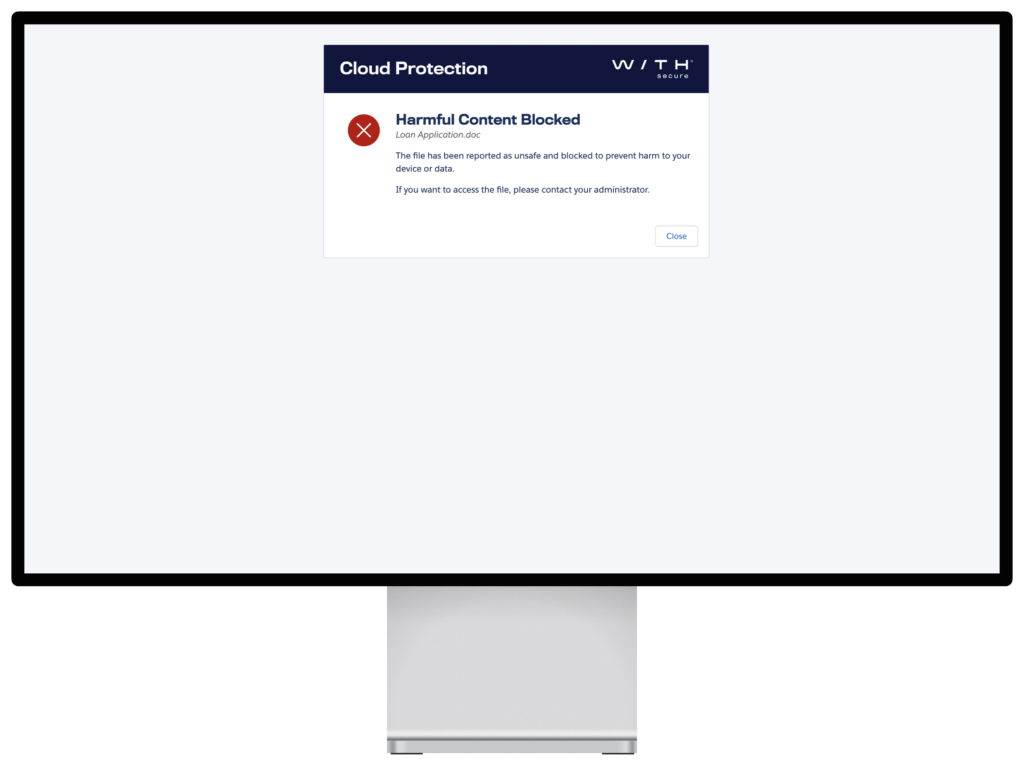
To prevent any compromise, the file is immediately isolated within Salesforce and substituted with a harmless text file, thereby averting accidental activation by support staff.
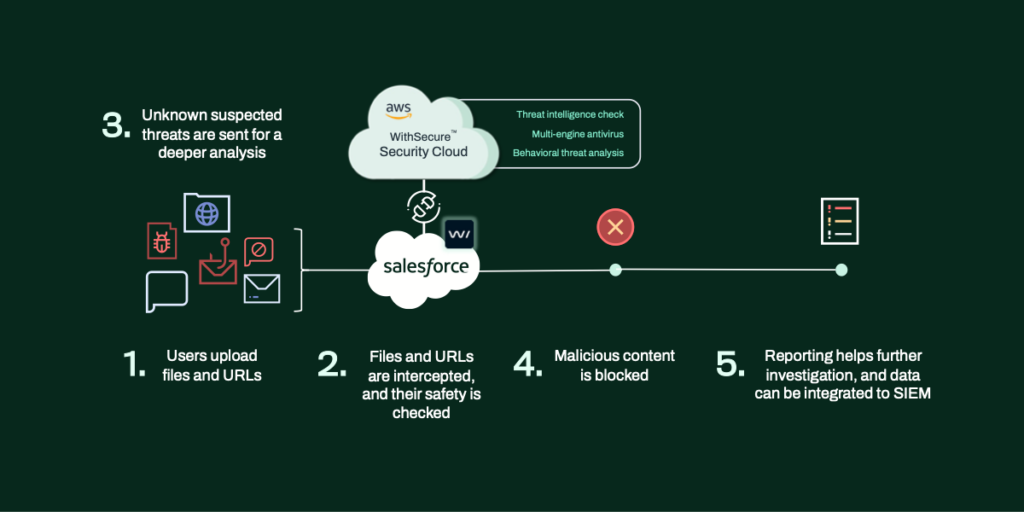
Simultaneously, Salesforce users attempting to access the file receive a prompt in their browser, alerting them to the potential threat—a message that can be tailored to fit your organization’s communication style.
In the background, administrators are alerted to the threat’s presence, provided with a detailed forensic report that chronicles user interactions with the suspect file, including the time of upload and the uploader’s identity.
The compromised file is proactively blocked across the Salesforce environment, eliminating the need for manual intervention.
Staying ahead of the threat
Don’t overlook the potential dangers of PDFs. Ensure every file upload, especially in Salesforce, is scanned. When selecting an anti-virus solution, opt for one that employs comprehensive threat detection techniques. Implement automated, real-time solutions and adopt a multi-layered defense strategy to safeguard your entire digital ecosystem.
Key takeaways
- PDF files can be deceptive carriers of malware.
- Salesforce, by default, does not scan for PDF malware.
- Essential to scan all uploads with a robust anti-virus.
- Choose anti-virus solutions offering signature-based and behavioral analyses.
- Employ automated defenses to rapidly counteract threats.
- Salesforce-native tools are optimal for system compatibility and performance.
- Trust in a multi-layered defense strategy to protect both Salesforce and associated devices.

