URL PROTECTION | SALESFORCE ANTI-PHISHING | URL SCANNING
Stop phishing attacks on Salesforce
Eliminate human error with real-time URL scanning on Salesforce
Scans at post and click
From short links to newly registered domains
Malicious URLs can silently infiltrate and compromise your Salesforce environment and its users. From phishing to malware and credential theft, these covert risks can disrupt your daily business operations and damage your trusted brand.
Stop phishing and URL-based threats
URL protection guards against phishing and malicious websites in real-time – upon upload and click.
Detect malicious URLs in files
Detect and block malicious URLs hidden inside files and behind QR codes uploaded to your Salesforce platform.
Block shortened URL threats
Every link is verified, whether shortened for convenience or masking a more sinister destination.
Don’t overlook phishing risks
Phishing is one of the most common and successful cyber-attack vectors. Malicious URLs form the backbone of these phishing schemes, designed to masquerade as legitimate links. These URLs typically redirect unsuspecting users to fraudulent websites, where they are duped into revealing sensitive information. As they become more sophisticated, distinguishing these URLs from safe ones becomes increasingly challenging, making them a potent threat within Salesforce environments.
URLs are used in credential harvesting, where attackers construct websites that mirror legitimate business services to steal login information. Once an unsuspecting Salesforce user enters their credentials, the attackers gain access to private systems and data, leading to potential identity theft and unauthorized system access.
URL protection
Stop phishing attacks in real-time
Detect and block malicious URLs at the time of post
Prevent Salesforce users from accessing malicious websites used in phishing attacks
Detect malicious URLs in real-time at the time of click
Prevent Salesforce users from accessing malicious websites used in phishing attacks
Block unwanted website categories
Keep your Salesforce clean of questionable web content categories like gambling sites
Detect newly registered domains
Web domains can be filtered out by their age, keeping emerging phishing sites out
Detect malicious short links
Analyze the true destination of URLs, and identify masked phishing links behind shortened links
Scan URLs in Salesforce standard and custom objects
Phishing detection covers both Salesforce standard and custom objects
Malware risks behind URLs
URLs can serve as trojan horses for malware spreading. Clicking on a seemingly benign link can trigger the download and installation of harmful software. Malware spread via URLs may range from spyware, recording every keystroke, to ransomware, which can lock an organization out of its own data. This underscores the critical need for vigilance against URL-borne threats within Salesforce, as every file or link interaction could be a potential vector for infection.
Some cyber threats do not even require user interaction, such as drive-by downloads. Merely visiting a website with malicious intent can cause malware to download and install automatically. These URLs exploit vulnerabilities within the browser or its extensions, carrying out actions without the user’s knowledge or consent. This silent havoc often goes unnoticed until significant damage has occurred.
Attackers see Salesforce as an effective distribution channel
Salesforce’s expansive platform is full of potential entry points for attackers. From custom fields to community posts, any area where a URL can be entered poses a risk. These open text fields, especially when accessible by external users, increase the vulnerability of the environment to malicious URLs.
Attackers adeptly leverage these entry points, exploiting Salesforce’s features to inject harmful URLs. For instance, email-to-case or web-to-case functionalities, which are meant to streamline customer service processes, can be subverted to introduce phishing links or malicious URLs, directly targeting customer service representatives who may unwittingly click on them.
What makes your Salesforce even more attractive to the cyber criminals is the ecosystem of connected systems that integrate to it. This creates an effective third-party supply chain for the attackers’ benefit.
Evolving threats: it’s not enough to just detect threats when they come in
The safety of a URL is not a constant; it can change from safe to dangerous in moments. Malicious actors can hijack legitimate sites or dynamically generate harmful URLs, making time-of-click protection a necessity. Such security measures evaluate the URL as it’s accessed, not just when it’s received, accounting for real-time threat emergence.
The convenience of shortened URLs in space-constrained communications is undeniable. However, these shortened links also provide a perfect cover for obfuscating malicious destinations, allowing attackers to hide their true intentions behind a veil of legitimacy. This tactic is particularly concerning in environments like Salesforce, where such links could be distributed widely with a single click.
Phishing attacks are more common, and attackers more crafty
Salesforce has highlighted phishing as the paramount concern for IT leaders. More data supports this concern. According to IBM, 41% of cyber attacks deploy phishing techniques, leveraging the familiarity and trust of public-facing applications. More alarmingly, IBM reports that 26% of these phishing campaigns specifically target such applications, with a further 16% of attacks successfully abusing legitimate user accounts to bypass security defenses. New tools such as FraudGPT are making it easier than ever for cyber criminals to launch sophisticated phishing attacks regardless of their skill levels.

This quantifiable data emphasizes the need for comprehensive security against URL-based threats – especially within Salesforce environments, where phishing attempts can blend seamlessly with regular operations. We’ve detected that approximately 1% of the millions of URLs scanned from large enterprises and critical public entities globally are malicious. It’s a big vulnerability without anti-phishing measures.
A real-life Salesforce phishing incident scenario
Let’s break down a real cyber attack that happened via Salesforce, as observed by our incident response consultant, showing how the attack unfolded and what was done to fix it.
- Initial compromise: A phishing email, which looked normal but contained a dangerous link, got through the email security and ended up in the company’s Salesforce system.
- The lure: Inside Salesforce, employees found the document from the phishing email. Clicking on the link in the document led them to a fake webpage set up by the hackers.
- Credential capture: The fake webpage tricked employees into entering their login details, including their extra security codes (tokens), which the attackers then stole.
- Unauthorized access: The attackers used these stolen details to get into the company’s Microsoft systems without permission. This was noticed because of unusual sign-ins from other countries.
- Detection: The company took a closer look at one employee’s laptop after noticing these strange sign-ins. They found that the laptop had visited some suspicious websites, pointing to an outside attack.
- Full exposure: Further investigation connected these signs back to the phishing email in Salesforce. This showed that the company’s normal security wasn’t enough to stop such clever attacks.
- Counteraction: Once the company knew about the breach, they stopped the stolen login details from being used and strengthened their security to prevent this kind of attack in the future.
This attack shows that cyber threats can sneak in through Salesforce and that usual security systems might not catch them. Companies need to have strong, up-to-date defenses that look for threats in real time and can check everything thoroughly if there’s an attack. It’s a reminder that being ready for all types of attacks is important for keeping Salesforce and other systems safe.
URL protection deep-dive
URL Protection: your anti-phishing layer
URL Protection in WithSecure™ Cloud Protection for Salesforce proactively prevents Salesforce users from accessing malicious or unwanted content across your custom objects and fields and the following Salesforce standard objects in real-time:
- Chatter posts and comments
- Inbound and outbound email messages
- Case comments and descriptions
- Web-to-lead descriptions
- Task comments
Real-time phishing protection against evolving URL threats
WithSecure™ Cloud Protection for Salesforce actively combats phishing threats. As users interact with Salesforce, they might upload or click URLs without knowing their safety – or with malicious intents. WithSecure™ Cloud Protection for Salesforce scans URLs on Salesforce without delay, both at the time of upload and when clicked. This ensures users are not exposed to and are not spreading harmful content, keeping your Salesforce environment safe and trusted to all users interacting with it.
You can configure Click-Time URL Protection separately.
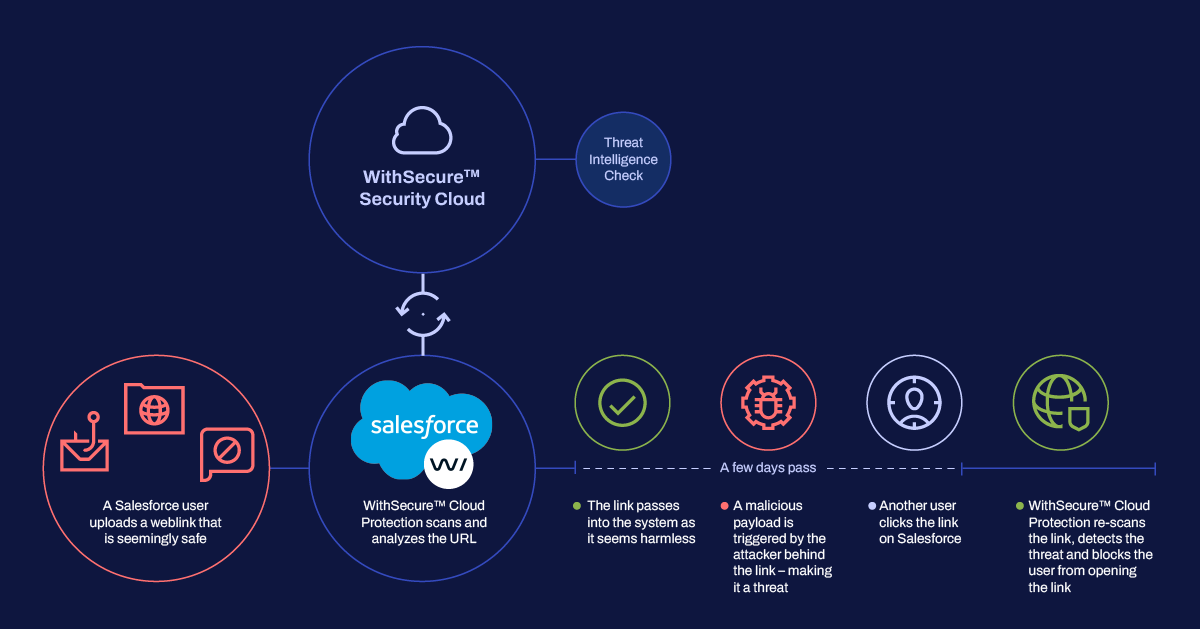
URL scanning inside files uploaded to Salesforce uncovers stealthy tactics
Not just visible links, but malicious URLs within files are a concern too. File Protection capability automatically scans and blocks malicious URLs hidden in files uploaded to Salesforce. The solution also detects malicious destinations behind QR codes, effectively halting any quishing attacks targeting your Salesforce.
Advanced threat analysis stops sophisticated attacks
WithSecure™ Security Cloud doesn’t just skim the surface. It conducts a detailed, multi-layered content analysis. Suspicious URLs that pass initial reputation checks are escalated for a more in-depth review to WithSecure’s cloud-based threat analysis platform. This approach ensures comprehensive protection, catching threats that might slip past traditional screening methods.
Shortened URL scanning unmasks links’ true destinations
Shortened URLs, while convenient, can hide risks. WithSecure Cloud Protection for Salesforce actively detects and blocks these hidden threats, ensuring the true destinations of links are safe.
Block access to newly registered domains
Cybercriminals often register new domains to evade reputational URL checks. Research indicates that over 70% of domains younger than 32 days are malicious or suspicious. You can actively block these domains by setting age thresholds at 7, 14, 30, 60, or 90 days, effectively filtering out potentially harmful new sites.
Automated threat remediation
When harmful content is identified, it’s automatically blocked or removed. Administrators and security teams receive alerts, and users are informed about the action taken. This proactive approach means threats are stopped before causing harm, and teams can respond swiftly to potential breaches.
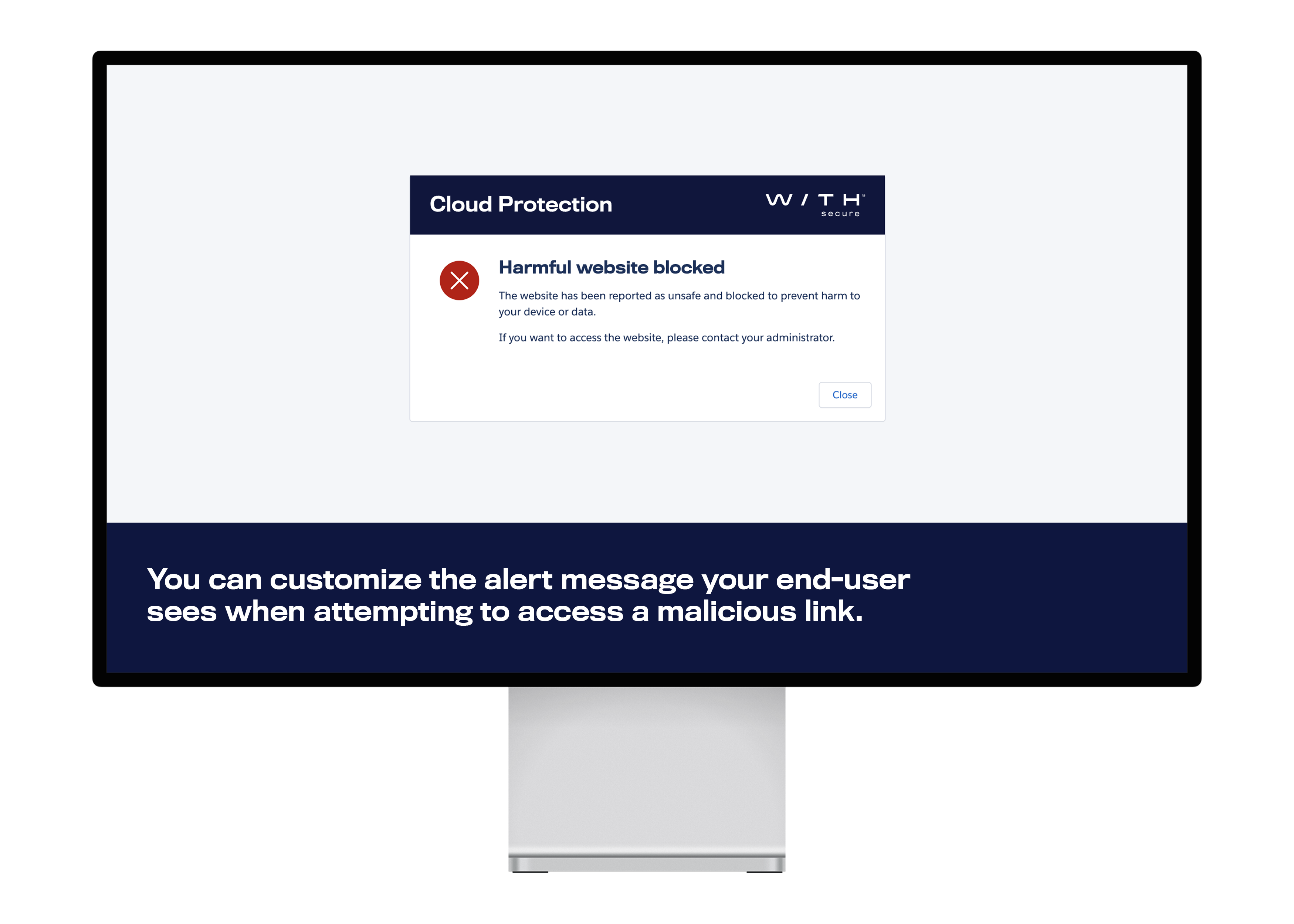
Content filtering wipes out unwanted websites
URL Classification allows you to prevent access to sites that may not be work-related or could pose a security risk. You can make Salesforce a safer workspace by limiting access to websites across 28 different categories from gambling to hacking and more.
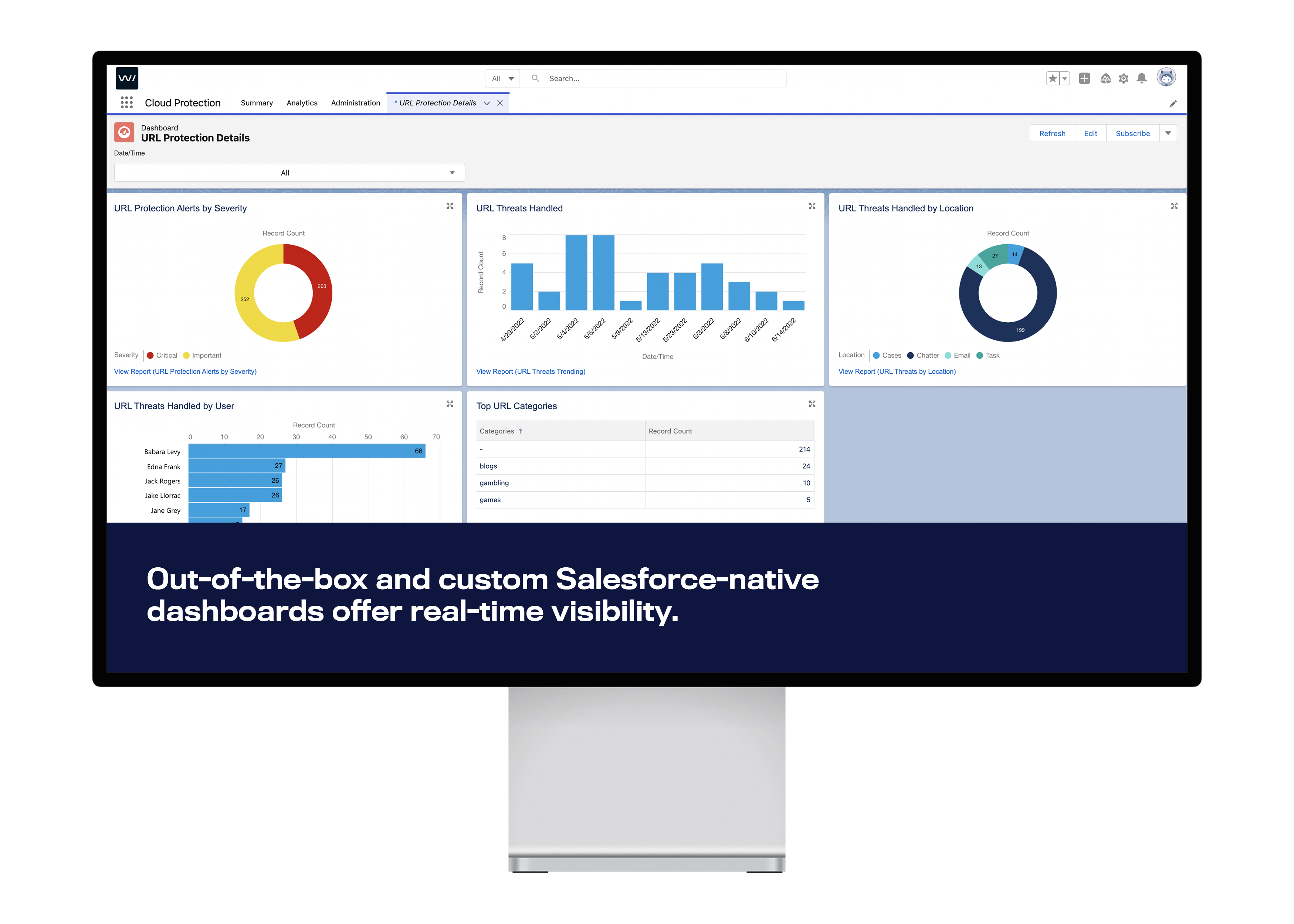
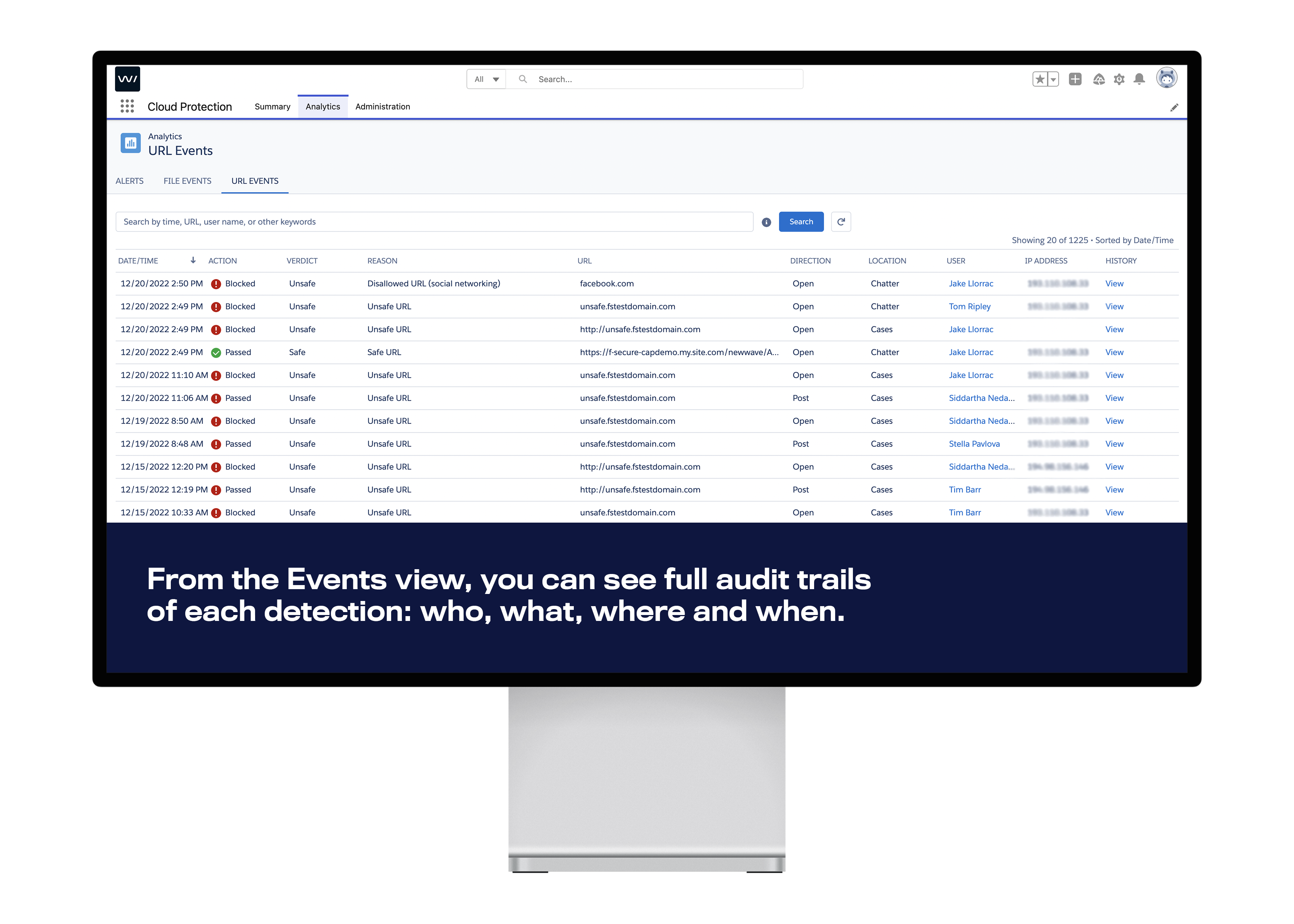
Security visibility through reports and analytics
Monitoring and responding to threats is made straightforward with detailed reporting and analytics. These tools give a clear view of the URL protection status, offering timely insights and complete audit trails. It’s about not just detecting threats but understanding them to prevent future risks.
BOOK A DEMO
Secure your Salesforce today
Tailored for high compliance sectors, our certified solution safeguards Salesforce clouds for global enterprises, including finance, healthcare, and the public sector.
Fill the form and get:
Free 15-day trial
Personalized Salesforce security risk assessment report
Demo and a solution consultation
Support from our experts with setup and configurations
